During the first quarter of 2015, PhishMe, a security firm specialized in tracking phishing activities, says it recorded a 789 percent increase in phishing activity compared to Q4 2015.
The PhishMe team says it detected 612 separate phishing waves that were carrying malware to over 6.3 million victims.
This number is down compared to Q4 2015, when the company recorded 662 separate waves, but the number of affected users is now higher than ever before.
Ransomware now accounts for 50% of all phishing email spam
In most of these cases, PhishMe experts claim that the favorite malware attached to these phishing emails was ransomware, which accounted for half of the total payloads by the end of March 2016.
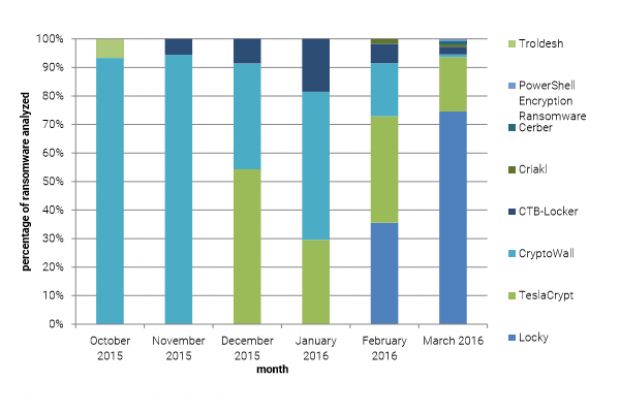
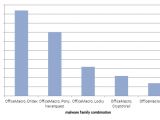
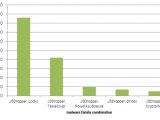
The ransomware payload changed across the first three months. In January, the most encountered threat was TeslaCrypt followed by CryptoWall, in February it was TeslaCrypt, Locky and then CryptoWall, and in March, Locky was dominating the market.
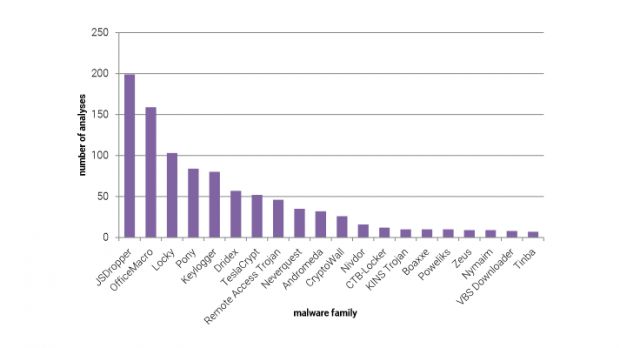
PhishMe says that by the end of March, three in four ransomware payloads encountered in phishing emails were Locky, mainly delivered via malicious JavaScript file attachments.
Overall, Locky infections accounted for one in eight ransomware payloads in the whole quarter, which is significant, taking into account that Locky appeared mid-January.
PhishMe's report stops in March, but recently, various other security firms have also reported of seeing one of the biggest spam floods in recent years distributing the Locky ransomware in May.
JS-based distribution model gains momentum
Furthermore, PhishMe says that crooks also started using malicious JavaScript files packed as ZIP files, attached to phishing emails, delivering everything from the aforementioned Locky ransomware to the Poweliks click-fraud bot and to famous and dangerous Dridex banking trojan.
Macro malware, or the practice of sending Office docs that require users to enable macro support in order to view the content, has also remained a strong alternative for delivering malware through phishing emails. PhishMe says that most of the time crooks used this method to deliver the Dridex and Neverquest banking trojans.
Both Locky and Dridex seem to be dominating the phishing ecosystem for both the JS and macro-based malware distribution models. PhishMe, just like other security firms, intimates that there might be a connection between the two.
"Locky and Dridex similarities imply collaboration between subsets of threat actors," the team noted in its recently released Q1 2016 Malware Review report.
 14 DAY TRIAL //
14 DAY TRIAL //