A new ransomware strain that appeared last week is giving users headaches as it seems to be improperly encrypting files or using a damaged decryptor, leaving victims with their data locked, even after paying the ransom.
Named Coverton, this is your typical crypto-ransomware, working just like many others that came before it.
Researchers currently don't know how the ransomware spreads, but it's probably spam, just like all the other ransomware infections. Once it reaches a victim's computer, the ransomware adds itself to the computer's start routine and then begins encrypting their files.
Coverton will search and lock 950 file types
Coverton targets a whopping 950 different file types, by far the most we've seen in a ransomware strain for a while now. Once finished, it appends the .coverton, .enigma, or .czvxce extensions at the end of encrypted each file.
The ransomware uses an unbreakable combination of AES and RSA encryption. Ransomware experts from Bleeping Computer say that Coverton contains no encryption flaws to leverage in creating a decrypter.
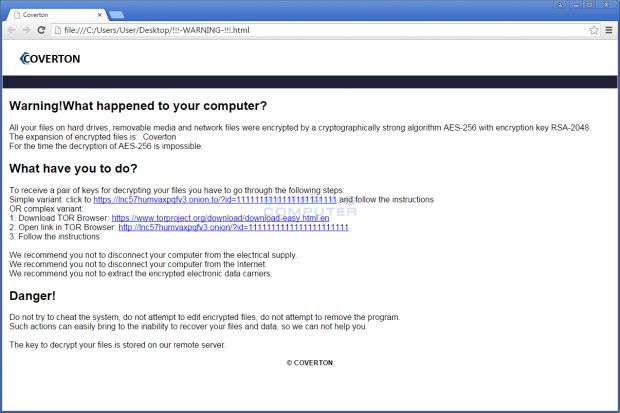
As usual, the ransom note, in HTML and text format, is left in every folder where Coverton encrypted files. These files contain instructions on how and where to pay the ransom. To recover their data, users have to pay 1 Bitcoin (~ $400).
Coverton also deletes shadow volume copies to prevent the user from recovering older versions of their files from their hard drive.
Coverton payments will stop coming if the decryption process fails
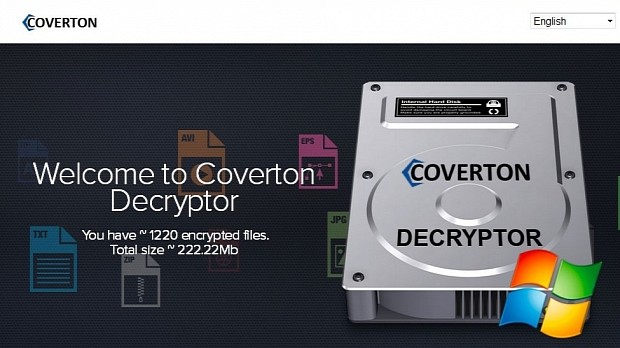
Up to this point, most ransomware variants work in the same way. Coverton managed to distinguish itself by not keeping its promise of decrypting files after users pay the ransom.
While other crypto-ransomware families like Locky, TeslaCrypt, CTB-Locker, or CryptoWall would never dare to anger users, it appears that Coverton's creators have not double-checked their decryption process.
There have been numerous reported cases where Coverton victims who paid the ransom didn't manage to decrypt their files with the decryptor provided by the ransomware's authors.
If the authors of this ransomware don't get this decryption process fixed and do it in a hurry, most users would cut their losses and not pay the ransom if they know for sure they won't recover their files.
 14 DAY TRIAL //
14 DAY TRIAL //