Between the end of April and the start of May, security firm Rapid7 conducted a series of Internet-wide port scans that covered the entire IPv4 Internet, for the purpose of unveiling the most exposed and vulnerable ports.
The company scanned for 30 popular protocols, both encrypted and unencrypted. Their findings show that companies are exposing services over the Internet, which should not happen.
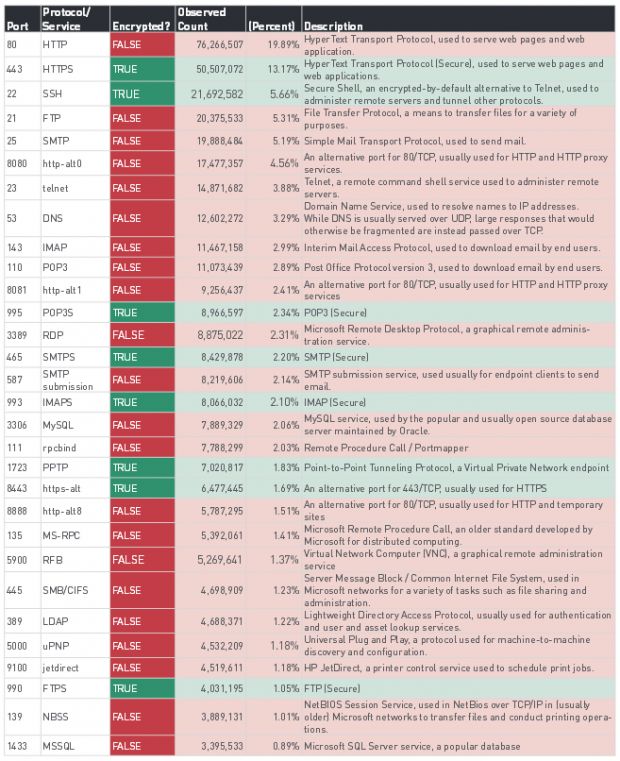
In fact, Rapid7 claims it discovered 14.8 million open Telnet ports that can be accessed by anyone with a working Internet connection.
22 years after the invention of SSH, Telnet is still well & alive
Whether these devices use or don't use a password is irrelevant. Because Telnet traffic is not encrypted, an attacker only needs to sniff local communications to intercept login operations.
While you certainly won't find Telnet enabled on high-grade Cisco routers, the protocol is extremely popular with IoT devices.
Rapid7's finding explains why many botnets these days rely more on IoT devices and SOHO routers than infected desktop stations. It is far easier for an attacker to brute-force an open Telnet port rather than A/B test spear-phishing email templates and tricky AV-evading Windows malware.
SSH is winning over Telnet. Finally!
The good news is that, when taking a look at the data in a historical context, Rapid7 says that SSH adoption is much higher when compared to Telnet, meaning manufacturers and end consumers are finally starting to understand why SSH was invented to begin with.
"The prevalence of SSH instead of telnet seems to indicate that SSH is winning out in production, as system administrators clearly prefer SSH over telnet," the company concluded in its report. "But, there is still ample attack surface for passive monitoring of remote administration tasks that continue to rely on telnet."
Overall, Rapid7 found 21.6 million open SSH ports available online, third overall, behind HTTP (76.2 million) and HTTPS (50.5 million).
But Telnet ports weren't the only "questionable" open ports found available via the Internet. The security firm's report also shows over 20.3 million open FTP ports, over 8.8 million RDP (Remote Desktop Protocol) ports, over 7.8 million MySQL ports, over 5.2 million RFB ports (used for Virtual Network Computer - VNC connections), and over 3.3 million MSSQL ports.
The security firm didn't find any link between the GDP of the local economy and the proliferation of insecure and open protocols, proving that good security practices aren't something you pinpoint with a red dot somewhere on a map.
You can find more details, statistics, and some very weird graphs in Rapid7's National Exposure Index - Inferring Internet Security Posture by Country through Port Scanning report.

 14 DAY TRIAL //
14 DAY TRIAL //