Hacking group OurMine has managed to hijack the official page of whistleblowing site WikiLeaks, but despite reports of a server hack, it turns out the attack was actually just a simple DNS spoof.
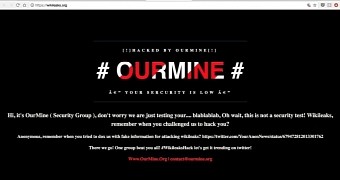
The WikiLeaks homepage was replaced with a black background on Thursday, with hacking group OurMine leaving a message to mock the organization led by Julian Assange and Anonymous hackers for undermining its hacking abilities.
“Hi, it’s OurMine ( Security Group ), don’t worry we are just testing your… blablablab, Oh wait, this is not a security test! Wikileaks, remember when you challenged us to hack you? Anonymous, remember when you tried to dox us with fake information for attacking wikileaks? There we go! One group beat you all!” the message posted by OurMine read.
WikiLeaks: Servers not breached
But despite claims that WikiLeaks suffered a breach of servers, the organization explained in a series of tweets that the defaced website was the result of a DNS spoof.
A DNS spoof, also called DNS poisoning, is an attack method that targets the DNS servers of a website, with hackers attempting to reroute traffic to a page they control. Visitors of the website are thus redirected to a different page, with files and servers not exposed in any way.
WikiLeaks confirmed on Twitter that “servers have not been hacked,” with Julian Assange himself confirming that “there have been two types of Internet infrastructure (DNS) attacks.”
The defaced page was quickly removed shortly after it went online and the WikiLeaks website is now working normally.
In separate news, WikiLeaks yesterday uncovered a new CIA hacking toolset that targeted the Windows boot sector and was used by the agency to compromise Windows XP and Windows 7 computers. Codenamed Angelfire, the project consisted of 5 tools with different purposes that would have allowed the CIA to deploy additional payloads on the target systems.
WikiLeaks servers have not been hacked. — WikiLeaks (@wikileaks) August 31, 2017
 14 DAY TRIAL //
14 DAY TRIAL //