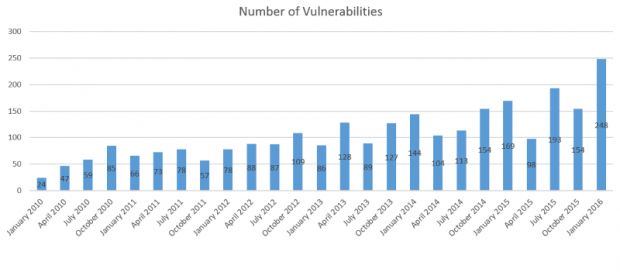
Oracle's January 2016 CPU (Critical Patch Update) was released yesterday, and the company's developers outdid themselves by fixing a record number of 248 security bugs, more than they had ever done in any previous CPU.
The previous record was of 198 patches, set during Oracle's July 2015 CPU.
Analyzing the January CPU, most of the vulnerabilities can be found in enterprise and cloud-based products, with very few affecting Oracle's flag products like MySQL, Java, and the Oracle database.
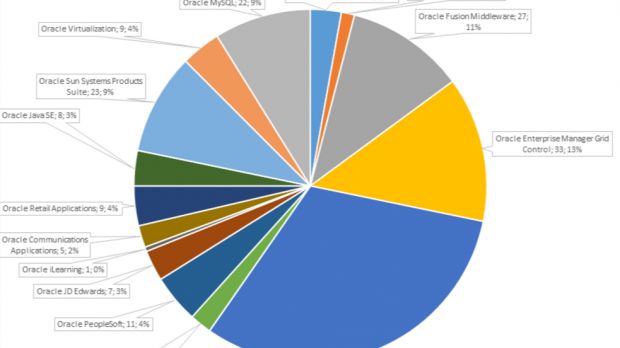
78 of these 248 security updates were in Oracle's EBS (E-Business Suite), by far the most patched Oracle application and barely missing the all-time record for the highest number of security bugs, currently held by Flash Player 20.0.0.228, which fixed 80 critical vulnerabilities in one go in December 2015.
Other Oracle applications with a large number of bugs fixed in this release include the Oracle Enterprise Manager Grid (33), the Oracle Fusion Middleware (27), Oracle Sun Systems Products (23), and Oracle MySQL (22). Java had only 8 fixes while the Oracle database featured only 7.
Five Java and GoldenGrid bugs allowed attackers to take control of PCs
Some of the most critical issues fixed by Oracle include five bugs that had a CVSS severity score of 10 out of 10.
The first three, CVE-2016-0494, CVE-2015-8126 and CVE-2016-0483, are found in Java's 2D and AWT subcomponents, and all allow attackers to take control of the operating system by executing arbitrary code on the machine.
The fourth and fifth issues, CVE-2016-0451 and CVE-2016-0452, are found in Oracle GoldenGate, a real-time, log-based change data capture, and delivery system that also allows attackers to take over Windows boxes through arbitrary code execution on the affected machines.
On top of these, you can throw two XXE (XML External Entity) vulnerabilities discovered by ERPScan in Oracle's E-Bussiness Suite (EBS).
"Due to the threat posed by a successful attack, Oracle strongly recommends that customers apply CPU fixes as soon as possible," Oracle advises. "Until you apply the CPU fixes, it may be possible to reduce the risk of successful attack by blocking network protocols required by an attack."
 14 DAY TRIAL //
14 DAY TRIAL //