Cloud service providers are failing when it comes to protecting their clients against the recently disclosed DROWN attack, with only 33 providers having patched their servers from a total of 653 surveyed services.
A total of fifteen researchers revealed the DROWN attack on March 1, showing how an attacker could break HTTPS traffic by leveraging an older attack method from 1998 against SSLv2, even if the server's traffic was protected with newer and more secure TLS certificates.
Researchers said in their report that the DROWN vulnerability affected one in three websites running HTTPS. Skyhigh Networks, a cloud security company, explains that, during its scans, it detected 653 cloud service providers susceptible to DROWN attacks.
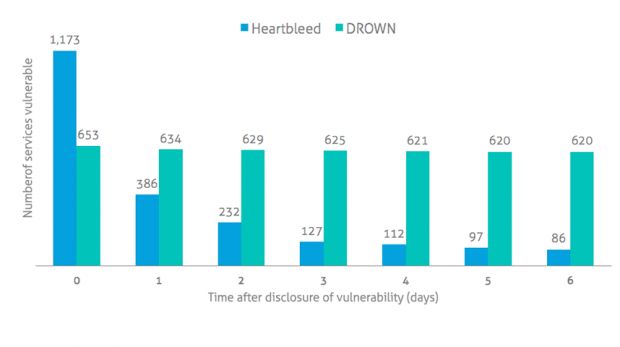
Repeating their scan every day over the following week, researchers claim that, seven days later, on March 8, 620 of the original 653 servers were still vulnerable.
Cloud providers did a better job of patching against Heartbleed
"What’s troubling about this critical vulnerability is how slow cloud providers have been in responding to patch their services against DROWN by disabling SSLv2 support," said Sekhar Sarukkai of Skyhigh Networks.
Compared to the infamous Heartbleed bug, the same statistics show how much cloud service providers have ignored DROWN. According to Skyhigh's scans, the company detected 1,173 cloud service providers vulnerable to Heartbleed attacks when it was first announced. One day later, this number was down to 386, and a week later, it was only 86.
That means that 92.7% of the initially affected cloud providers did their job and patched their servers. On the other hand, only 5.1% patched against DROWN.
On average, a company uses 56 DROWN-vulnerable cloud servers
Skyhigh states that 98.9% of enterprises that use cloud providers are bound to use at least one cloud service vulnerable to DROWN. The researchers estimate that each company uses on average at least 56 cloud servers susceptible to DROWN attacks.
The reason so many cloud providers failed to intervene may have something to do with the fact that the attack uses flaws in SSLv2. After a quick glance over the vulnerability report, a sysadmin for one of these companies may think that, just because their server uses TLS, they're safe.
But according to the researchers who discovered DROWN, if a server still supports SSLv2 or uses a private key shared with a server that runs SSLv2, then it is also vulnerable, in spite of the fact that it uses the more secure TLS protocol.

 14 DAY TRIAL //
14 DAY TRIAL //