A sinister Android application has managed to infect around 1 million users, being delivered right through Google's Play Store after managing to evade detection.
The app is called Brain Test and is a simple IQ testing utility, which comes packed with a combination of complex malware strands.
According to Check Point's research staff, the application was detected via the company's Mobile Threat Prevention system, first on a Nexus 5 device.
Because its owner, after receiving the malware alert, did not manage to uninstall the malicious app, this prompted Check Point's team to have a closer look at the source of the infection.
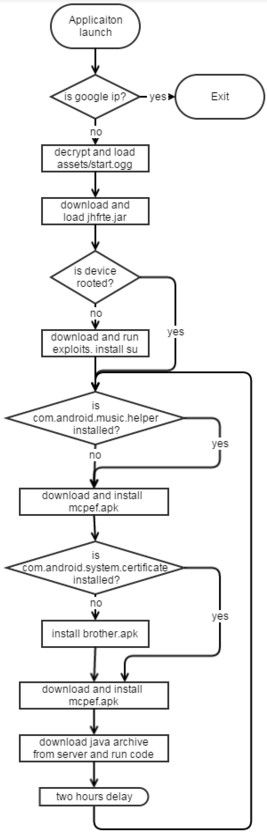
By reverse-engineering the Brain Test app, researchers found a very well-designed piece of malware, which allowed attackers to install third-party applications on the user's phone, after previously rooting the device and even managing to become boot-persistent.
Brain Test came with a complex detection avoidance system
Looking even further into the issue, researchers found a complex system that allowed the malware to avoid detection by Google's Bouncer, an automated app testing system that checks for known security issues.
The malware contained code that prevented it from executing if it detected it was being run from certain IP ranges, or domains containing “google”, ”android”, ”1e100.”
After managing to get around Bouncer's checks and getting installed on a user's phone, Brain Test would execute a time bomb function whenever the user would run it for the first time.
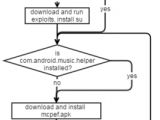
This function executed after a 20-second delay, once every 2 hours, and slowly downloaded and unpacked the necessary code to give itself root permission using a series of four chained exploits.
The malware had a smaller brother
Once root was achieved, Brain Test would then install another application called brother.apk, which would constantly check, alongside Brain Test, that the malware was installed and rooted. If any of these two apps was removed, once every two hours, the other would reinstall it.
Just two days ago, security researchers at Cheetah Mobile found a similar boot-persistent Android malware, this one called Ghost Push, distributed via various unofficial app stores around the globe.
Security researchers did not detail what the app's capabilities were, but taking into account it was talking to a C&C server and had root privileges, attackers could have instructed it to carry out a wide range of attacks, all which did not require any type of user interaction.
Check Point researchers informed Google of the malicious app on September 10, and its engineers had it taken down five days later. The app was subsequently reuploaded a few days later, but Check Point's Mobile Threat Prevention system quickly picked it up and informed Google again.
 14 DAY TRIAL //
14 DAY TRIAL //