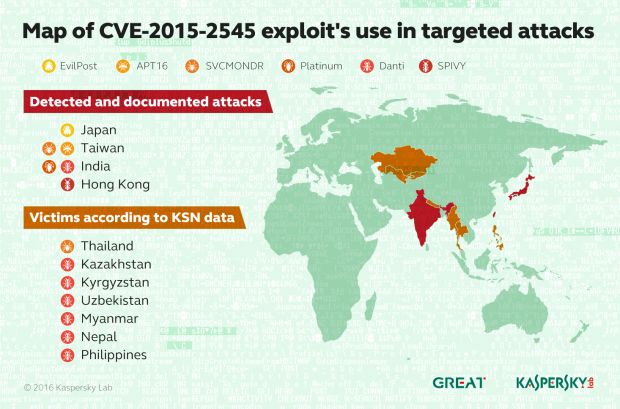
CVE-2015-2545 is the identifier of a security bug in Microsoft Office that has become very popular with many cyber-espionage groups around the world, such as Platinum, Danti, APT16, Ke3chang, and SVCMONDR.
CVE-2015-2545 allows an attacker to execute malicious code on the user's machine and take over their device by embedding a malicious EPS (Encapsulated Postscript) payload inside Office docs.
The bug affects Office installations running on 2007 SP3, 2010 SP2, 2013 SP1, and 2013 RT SP1, and was fixed in Microsoft's security bulletin MS15-099.
CVE-2015-2545 was a zero-day at the time it was fixed
In fact, Microsoft patched the issue to begin with because of a targeted cyber-attack. Back in August 2015, Microsoft's experts noticed the Platinum APT leveraged a never-before-seen exploit (called zero-day) against targets in South-East Asia, mostly against government agencies in Malaysia, Indonesia, China, and India.
The company patched the issue, later known as CVE-2015-2545, and all attacks immediately stopped, even if the Platinum group continued to operate.
Things quieted down for two months, and in November 2015, another cyber-espionage group, APT16, integrated the same exploit for a campaign aimed at news agencies and Taiwan politicians.
CVE-2015-2545 became very popular, very quickly
But things didn't stop here because, in December 2015, Kaspersky also reported on another group named EvilPost also employing the same exploit to target the Japanese defense sector.
CVE-2015-2545 was also used by the famous Carbanak bank cyber-heisters and also by an unknown cyber-espionage group that targeted pro-democracy organizations and supporters in Hong Kong this April.
In late May, Palo Alto Networks also brought to light new activity from the Ke3chang group that also used CVE-2015-2545 to target Indian embassies around the world.
New cyber-espionage groups surface and exploit the same Office flaw
The most recent revelations regarding this popular exploit come from Kaspersky, who released yesterday details about two new cyber-espionage groups also using this exploit, named Danti and SVCMONDR.
The security vendor said that the Danti group is a new APT, never before observed, active since 2015, with some ties to the NetTraveller and DragonOK groups. Kaspersky says that the group has targeted organizations in Kazakhstan, Kyrgyzstan, Uzbekistan, Myanmar, Nepal, and the Philippines.
Additionally, the group has also attacked Indian embassies in different countries, and it may be possible that Danti and Ke3chang are the same entity based on their MO and targeting tactics, but this information is currently unconfirmed.
The second APT Kaspersky discovered is named SVCMONDR, and security vendor says that first attacks using CVE-2015-2545 were seen in December 2015, against a Taiwanese security software reseller.
The common string connecting all these APTs is their Chinese connection, most security firms explaining that the goals of these APTs and the target they select are usually aligned with Chinese external policies.

 14 DAY TRIAL //
14 DAY TRIAL //