A CloudFlare engineer has discovered that about 10% of the Alexa Top 1 Million sites use an improper Cross-Origin Resource Sharing (CORS) policy that exposes users to data theft.
Cross-Origin Resource Sharing (CORS) is a mechanism that controls what server resources can be shared with other domains. CORS is a crucial part of the Same Origin Policy (SOP), a general set of guidelines that are at the core of the Web security model.
SOP forbids by default fonts and AJAX requests to work across different domains. CORS is a way for developers and server admins to control what resources can be accessed from/on other domains.
This wouldn't be an issue, except that sometimes, for technical reasons, some of these sites must be able to share resources with other websites.
Many sites expose users to CSRF and XSS attacks
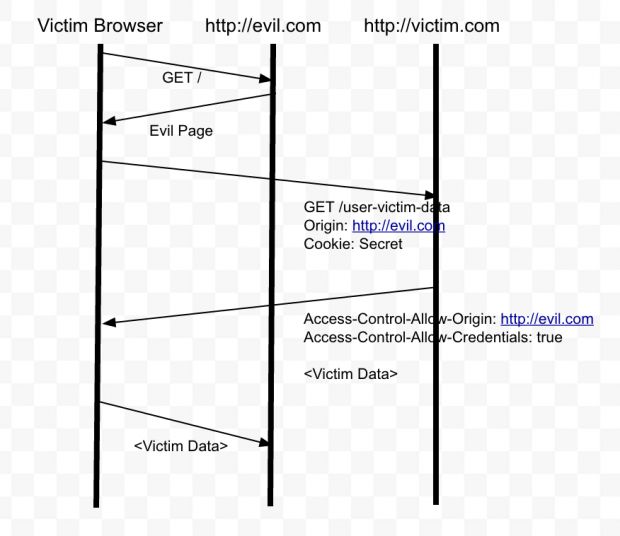
Evan Johnson, CloudFlare engineer, has discovered that many of the top websites on the Internet today allow resources to be shared outside of their domain. The problem is that the RFC standard that describes the proper CORS settings that need to be applied in this case is extremely convoluted and sometimes misleads developers.
Using a simple Batch script he put together, Mr. Johnson scanned the Alexa Top 1 Million sites and discovered a large number of websites with improperly configured CORS settings.
These misconfigurations open websites to CSRF (Cross-Site Request Forgery) and XSS (Cross-Site Scripting) vulnerabilities, often used by attackers to steal the user's private session details and log into their accounts to carry out fraudulent operations.
Mr. Johnson even put together a list of the vulnerable websites. Among them, we find sites for mobile health apps, Bitcoin payment portals, banking portals, trading portals, online shop builders, and many others. Ironically, some of the detected domains were also blacklisted by Google's Safe Browsing filter.
"Security is contextual. Not all of the sites in the dump are misconfigured, but it's a safe bet that a bunch of them are," Mr. Johnson explains. "Traditional sites that require a username and password with this configuration are almost certainly misconfigured."

 14 DAY TRIAL //
14 DAY TRIAL //