Continuing to look for clues after they unmasked the operator of the Ranscam ransomware as nothing more than a liar and scammer, Cisco researchers have found new evidence that links this individual to other ransomware families such as Jigsaw or AnonPop.
All these three ransomware variants, Ranscam, Jigsaw, and AnonPop, are part of a category known as "destructive ransomware" because they delete the user's encrypted files if they don't pay the ransom sum.
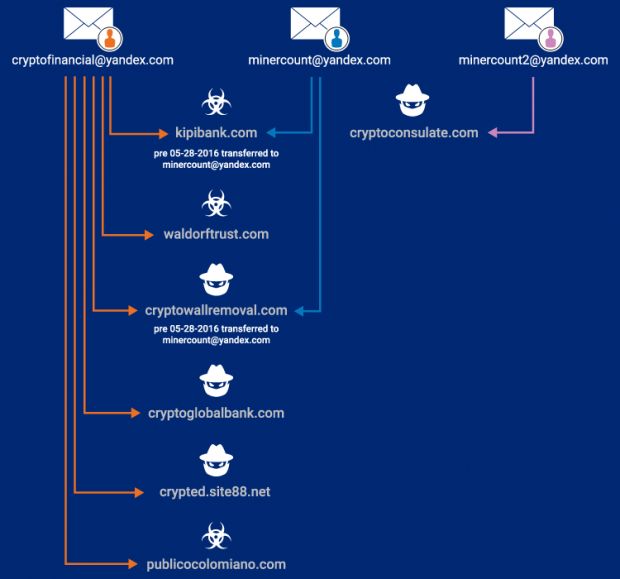
Cisco says that, because the Ranscam ransomware was only distributed from one single domain name, they started their investigation from there.
Three email addresses link all three ransomware operations
According to their findings, this domain was registered with the email address: cryptofinancial[@]yandex[.]com.
They also discovered that this email address was also used to register other domain names, which were later transferred to another registrant account that used the minercount[@]yandex[.]com address and featured the same phone number as the first account, hinting to be owned by the same individual.
Cisco says that some of these domains were used to deliver Jigsaw and AnonPop samples, but also other post-AnonPop-infection malware.
Furthermore, a third email address, very similar to the second, minercount2[@]yandex[.]com, was also used to registered domains that were hosted on the same servers that hosted the malicious domains.
Crook was active on programming and hacking forums
A search for the minercount username used for the second and third email addresses uncovered activity on forum and hacking forums.
In one of these forum posts, minercount was thanking the creator of a .NET code obfuscation utility. Both Ranscam and AnonPop used this obfuscator for their source code.
Furthermore, researchers found forum posts in which the user minercount linked back to domains registered using one of the three email addresses. In one of these forum posts, the crook was advertising a new ransomware variant for only $50.
Crook is currently spreading malware via Reddit
Cisco researchers also discovered Reddit threads that linked to the domains registered using those three email addresses. In some posts, the Reddit user, this time under the name of /u/cryptoconsulate, was distributing malware, including a new ransomware version.
Unsurprisingly to anyone at this point, the crook recycled one of the Bitcoin addresses he used for the Jigsaw ransomware, which tied him once more to Jigsaw ransomware distribution.
Cisco researchers are not 100% sure that minercount created the Jigsaw ransomware, but at this point, he looks like one of the major sources of Jigsaw distribution.
"[A] single actor could be responsible for multiple distinct variants in an attempt to maximize their profits, or as they refine their tactics in an attempt to maximize the amount of revenue they collect from victims," Cisco researchers conclude.
 14 DAY TRIAL //
14 DAY TRIAL //