John Matherly, founder of Shodan.io, a search engine for searching the Web for specific types of computers and technologies, has published a report in which he reveals how a three-year-old error in the default configuration of MongoDB has left many databases vulnerable to outside connections without proper authorization.
Mr. Matherly discovered around 30,000 exposed instances of the MongoDB NoSQL database which allowed attackers to connect to its data without any kind of authorization.
This left exposed 600 terabytes of data, which hackers could have easily gotten (get) their hands on without being required to enter a username & password combination.
Most of the exposed databases were cloud-based installations, running on services like Digital Ocean, Amazon, OVH, or Linode.
This problem was explained by Mr. Matherly by the arduous process of updating database images on a cloud-based infrastructure, which was also the cause of many data breaches in the past.
It took MongoDB developers three years to change one line of code
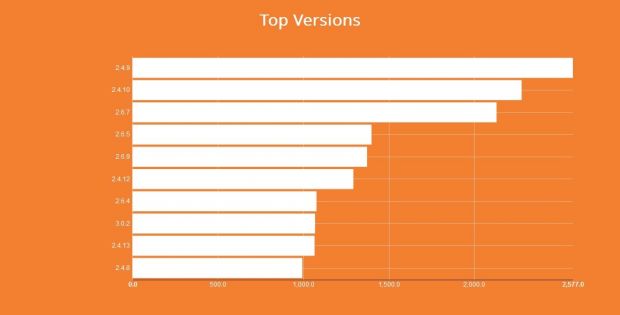
Digging into MongoDB's default configuration file and its change history on GitHub, the problem seems to have existed with version 2.4.14 and prior, but also some of the early 2.6.x versions which were in beta development alongside the 2.4.x branch.
In those older configuration files, MongoDB databases were left open to outside connections, a problem which classic relational database systems have been confronted and have gone to fix in the ‘90s.
NoSQL databases, being newer on the market, seem to be going through the same growing pains their relational counterparts have gone through in their early days, Mr. Matherly also implying some Redis versions might be vulnerable to this same configuration error as well.
Digging around even deeper, Mr. Matherly was surprised to find out this problem was reported back in February 2012, and it took the company three years to change the default DB config to a safer version, in late April 2015.
Update: Soon as we published the article, we were contacted by a MongoDB representative with an official statement from MongoDB's management as follows:
Kelly Stirman, VP of Strategy at MongoDB: “Recently a blog post was published that claimed some users had not properly secured their instances of MongoDB and were therefore at risk. As the article explains, the potential issue is a result of how a user might configure their deployment without security enabled. There is no security issue with MongoDB - extensive security capabilities are included with MongoDB."
“We encourage all users to follow the guidelines we prescribe for security. Security best practices are summarized here, or customers can contact MongoDB support. This is an important opportunity for everyone to ensure they are following security best practices.”

 14 DAY TRIAL //
14 DAY TRIAL //