During the first three months of the year, DDoS protection firm Imperva observed a series of interesting trends regarding the DDoS landscape. According to the company's latest quarterly report, both network layer and application layer attacks grew in size and sophistication.
One of the rising trends is for Mpps network layer DDoS floods. Mpps stands for "Millions of packets per second" and refers to attacks targeting networking equipment by sending massive amounts of packets, not necessarily enough to clog up the company's bandwidth, but sufficient to overwhelm and crash networking equipment such as switches and routers.
Network layer multi-packet attacks may be the next hot trend
Imperva experts say they mitigated on average a 50+ Mpps DDoS attack every four days and 80+ Mpps attacks every eight days.
"We estimate that high Mpps attacks are being used as an attempt to circumvent current-gen DDoS mitigation solutions," Igal Zeifman, senior inbound marketing manager for Incapsula explained.
"By now, the majority of mitigation services and appliances are highly effective in dealing with high Gbps assaults. However, [...] many of the same solutions are not be as capable of dealing with high Mpps scenarios, as they weren’t designed with high packet processing rates in mind."
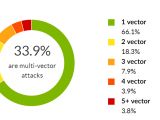
Another trend observed in network-level DDoS attacks includes the growth of multi-vector attacks. Imperva says that 33.9 percent of all the DDoS attacks it detected in Q1 2016 were multi-vector. A previous report by Neustar for Q4 2015 had this number at 17 percent.
Application layer attacks are getting smarter
On the other hand, for application-level attacks, Imperva says that it saw a rise both in the size of these attacks and their sophistication.
At the start of the month, the same Imperva was reporting on a new record for Layer 7 DDoS attacks set by the Nitol botnet.
Looking back over the entire quarter, besides this size increase, Imperva also noticed another trend. Botnet operators are beginning to deploy smarter bots (malware that infects computers to launch DDoS attacks).
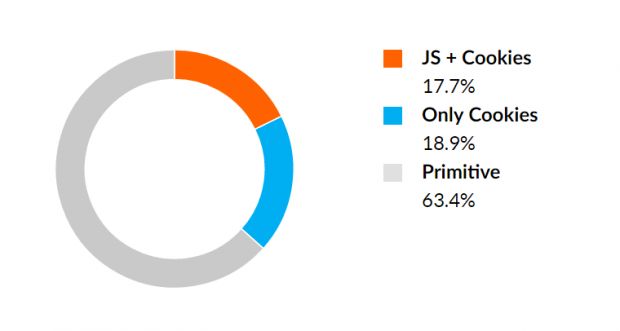
In the first three months of the year, Imperva saw bots that could accept and hold cookies and bots that can parse JavaScript code in 36.6 percent of all the DDoS traffic. This same number was only 6.1 percent in Q4 2015.
The reason is that DDoS mitigation services use either cookies or JavaScript code to distinguish between actual users (browsers) and automated traffic, so adding these capabilities to DDoS bots allow them to circumvent some protection systems. Imperva says that, in most of the detected cases, DDoS bots were masked as Chrome and Firefox using fake user agent strings.
For more details, Softpedia readers can check out Imperva's Global DDoS Threat Landscape Q1 2016.
 14 DAY TRIAL //
14 DAY TRIAL //