In a two-part investigation, security researchers from Israeli security firm Check Point have dug around in countless logs of telemetry data to get to the bottom of the Nuclear Exploit Kit (EK), one of the most popular crimeware kits today.
Exploit kits are scripts that crooks install on a server that, when a user visits a Web page, scans the victim's local PC setup for known software vulnerabilities and delivers an exploit that cracks their defenses and automatically installs malware without their knowledge.
Some of the most known exploit kits are Blackhole (now defunct), Angler (the most popular), Magnitude, and Neutrino. Also very popular is the Nuclear EK, which Check Point researchers have recently managed to track down and hack into one of its master servers.
Nuclear EK author lives in Krasnodar, Russia
According to researchers, the Nuclear EK is offered as MaaS (Malware-as-a-Service) by a crook living in Krasnodar, Russia. This man is suspected to be the EK's leading developer, but Check Point says that Nuclear is not a one-man job and that others are also almost certainly helping him manage the service.
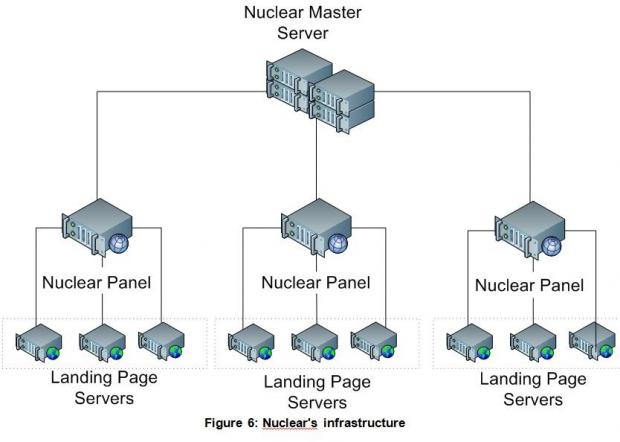
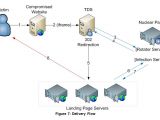
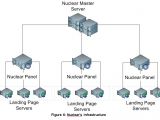
The EK's structure is simple. At the center resides the crook's main server, from where he manages and grants access to his infrastructure for all the other criminals who rent out his service.
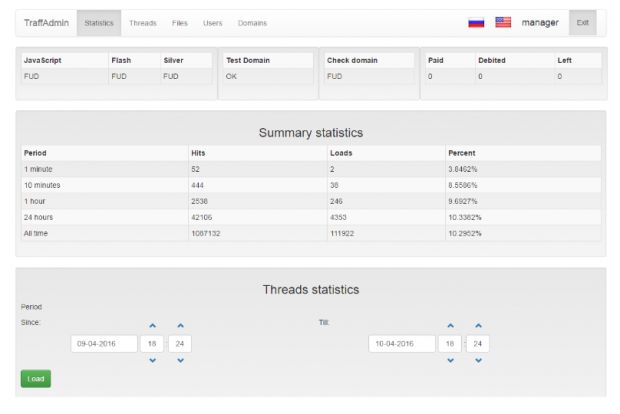
Anyone who rents a Nuclear EK from this man gets their own server with an easy-to-use control panel to view statistics and manage the malware that gets sent to users. Below this level are multiple smaller servers, called "landing pages," which host Web pages where users land and get infected with malware.
Check Point says that, at the time of its investigation, the company discovered 15 such servers. Based on server renting fees and the crook's prices, the security firm claims the man behind Nuclear makes around $100,000 (€90,000) per month.
Crooks with Nuclear EK infected nearly 2 million computers
During the period in which researchers had access to the Nuclear exploit kit infrastructure, they say that over 1,846,678 users accessed the landing pages.
Taking into account that on average 9.95 percent of all users who visit an exploit kit landing page get infected, researchers estimate that Nuclear managed to infect 184,568 computers.
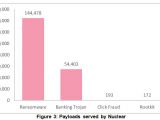
Crooks delivered 144,478 ransomware payloads, 54,403 banking trojans, 193 click fraud bots, and 172 rootkits. Over 110,000 of the ransomware infections were with Locky. Taking into account Locky's standard ransom price of 0.5 BitCoin, or $230, the crooks who rented the Nuclear EK made $12,650,000 (€11,182,000).
"We reviewed various aspects of Nuclear’s activity, including the control panel used by attackers, the general flow of its operation, the URL logic, the landing page, and the vulnerabilities the Exploit Kit uses to infiltrate machines," Check Point writes today. "Understanding Nuclear’s tactics in full will help security vendors to tackle it, and even defeat it completely."
For more in-depth information, Check Point is offering the Inside Nuclear's Core: Unraveling a Malware-as-a-Service Infrastructure (Part 1 and Part 2) reports as free downloads.

 14 DAY TRIAL //
14 DAY TRIAL //