It took crooks less than two weeks to weaponize the most recent Flash zero-day, which they're now using as a module inside the Magnitude exploit kit.
On May 8, Adobe pre-announced the release of a critical Flash security flaw exploited in the wild by attackers. On May 12, the company lived up to its word and patched the issue with the release of Adobe Flash Player 21.0.0.242.
The following day, FireEye researcher Genwei Jiang, the man who discovered the Flash exploit used in the wild, revealed the technical details of CVE-2016-4117, the identifier assigned to this security bug.
Surprisingly, CVE-2016-4117 was not a Web-based exploit, but an attack delivered via Office files that contained a Flash object embedded in their content.
Crooks were using this exploit to infect users with malware when they opened the Office document and allowed the Flash object to run. CVE-2016-4117 was successful in infecting all users who had Flash Player version 21.0.0.226 and earlier.
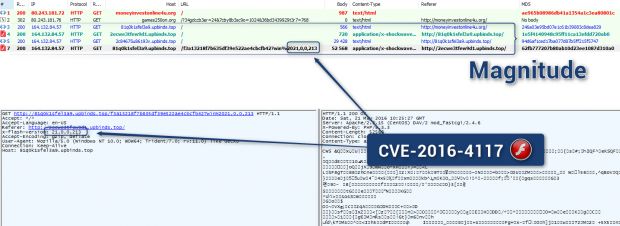
On May 21, nine days after Adobe put out a fix and eight days after FireEye revealed the zero-day's technical details, security researcher Kafeine announced he spotted the first instance of this flaw exploited online.
Kafeine detected a case of the Magnitude exploit kit trying to attack users with a weaponized CVE-2016-4117 exploit that was firing every time a user would access a page and had a Flash version of up to 21.0.0.213 installed.
At the start of April, Kafeine himself also discovered another Flash zero-day, CVE-2016-1019, exploited to deliver Cerber and Locky ransomware.

 14 DAY TRIAL //
14 DAY TRIAL //