Threat actors are circulating a new type of infostealer trojan that will search for eleven file types and upload them to a C&C server. The files it targets are specific to enterprise environments, being mostly extensions associated with Microsoft Office applications.
Based on a sample of the trojan, crooks are distributing this threat as a file named Aug_1st_java.exe, which currently has a very low detection rate on VirusTotal, 34/55.
The distribution method is currently unknown, and it could be either via spam or via watering hole attacks. As is the case with almost all malware programs today, when users install this trojan, it will modify the Windows Registry to gain the ability to start automatically after the user reboots their computer.
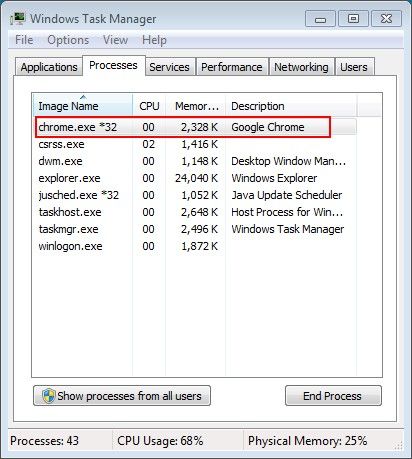
Trojan disguises as Google Chrome process
Current versions of this yet unnamed infostealer trojan disguise themselves as the process of the Google Chrome browser, as pictured below.
Right after it is installed, the trojan will collect data about the current computer and direct it to its C&C server, to which it sends communications via the MSMQ (Windows Message Queuing) protocol.
The data it gathers includes the computer's name, the username, the version of Windows, the service pack version, and a list of currently installed applications.
Trojan uses hacked websites to hide its C&C server
The server it was caught communicating with by Lawrence Abrams, malware analyst for Bleeping Computer, is located at web4solution.net.
When he contacted the company in charge of the domain, it came to light that their site had been compromised and loading a hidden iframe that relayed traffic to the real C&C server.
The company cleaned their site, but the C&C server remained active and will continue to work, presumably with another redirect through another hacked website.
Infostealer targets only eleven file types
After the trojan reports to the C&C server, its malicious operations don't stop here, and it will start scanning the infected computer for eleven file types: INP, SQL, PDF, RTF, TXT, XLSX, XLS, PPTX, PPT, DOCX, and DOC.
As you can see, most of them are Office-specific extensions, but others, like INP (Abaqus/CAE, used in engineering), SQL (extension used by database software), and PDF (Adobe Reader extension, document file), are for proprietary software usually found in enterprise networks.
The trojan will upload all the files with these extensions to its C&C server and then write a log at C:Users[username]uninst.dll.
"Corporate cybercrime and information theft has become a very lucrative business for malware developers," Abrams explains. "Not only does it allow them to steal corporate secrets to sell to the highest bidder, but it can also provide them with undisclosed financial reports that that can be used on the stock market."
UPDATE [August 16, 2016]: Malwarebytes has also published an analysis of this trojan, which they nicknamed Shakti.

 14 DAY TRIAL //
14 DAY TRIAL //