Malware developers have used two legitimate developer tools to create and help power an infostealer trojan that targets Mexico's second-largest bank and has infected users living in Mexico and the US.
Experts say the trojan actively targets Windows XP, WP 64-bit, and Server 2003, all operating systems which Microsoft officially stopped supporting a long, long time ago.
The crooks still need to work on the trojan's dropper
The trojan is relatively new and was first detected via a spam campaign. Zscaler security researchers say its distribution method leaves a lot to be desired, which is a good thing for its users since they can easily detect the trojan.
Crooks have always liked to disguise their malware under fake extensions, as malware.pdf.exe, and then switch the malware's app icon to make it look more authentic.
This trojan fails at the last step, and it forgets to embed the icon image, showing a file with a PDF extension, but with an executable's icon, which should ring alarm bells right away for any experienced Windows user.
Abusing open source tools for evil
In cases where the user is careless and launches the trojan into execution, this first-stage file will download the actual trojan payload, which is immediately started. Additionally, the trojan fetches two DLLs, which are nothing more than the Fiddler network debugging toolkit and the JSON.NET library.
Both are tools used by software and Web developers working with .NET apps, and no antivirus engine will ever flag them.
The purpose of these two DLLs is simple. Fiddler will be used to set up a local proxy server on the user's computer, and will intercept any traffic the trojan tells it to. Fiddler is capable of intercepting both HTTP and HTTPS Web traffic.
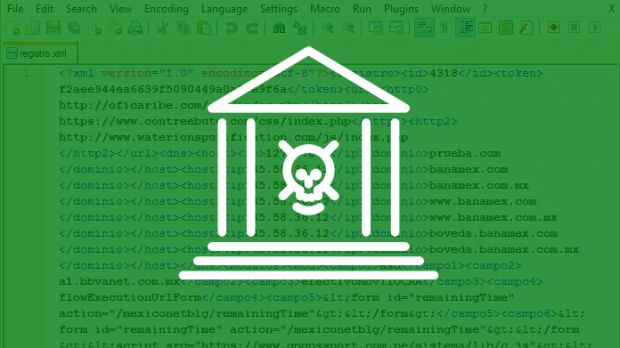
After launching into execution, the trojan begins talking to its master server, from where it receives a configuration file every ten minutes. Here's where JSON.NET comes into play, because this config file, sent as a JSON response, is taken and converted to XML, and saved on the local computer.
Trojan used to redirect users to phishing pages
Fiddler reads this file, and will know which traffic to intercept, for which URLs, and where to send it.
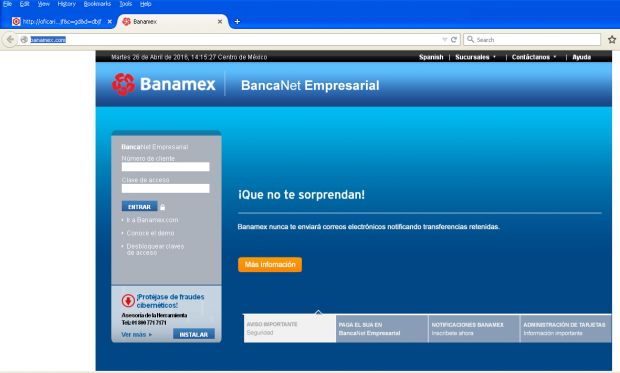
Zscaler says that it currently detected the trojan targeting only users of Banamex, Mexico's second-largest bank. Security experts say the trojan does not read the traffic and does not extract banking credentials, but only uses Fiddler and the XML configuration file to redirect the user's traffic to an attacker-controlled server.
Here, the crook serves a fake banking portal, where the user enters his Banamex banking account credentials, which are then recorded on the crook's server.
"We regularly see multiple .NET based malware payloads but this particular Infostealer Trojan caught our attention because of the use of popular application libraries like Fiddler & Json.NET in its operation," the Zscaler team noted. "The authors can easily add more targets [banks] given that they are actively updating the list every 10 minutes."

 14 DAY TRIAL //
14 DAY TRIAL //