Three new types of reflection DDoS attacks were observed by Akamai SIRT (Security Intelligence Response Team) being used in the wild from March to September 2015, utilizing three new amplification channels, namely NetBIOS name servers, Sentinel licensing servers, and RPC portmaps.
Reflection DDoS attacks (also known as R-DDoS, DRDoS, or Distributed Reflective Denial of Service) are not new, but they are not the most common DDoS attacks either.
An intro to reflection DDoS attacks
The way reflection DDoS attacks work is simple. An attacker sends a network packet to another user. The packet is intentionally corrupted but is also spoofed with an origin network address belonging to the victim the attack wants to flood.
Because the packet is corrupted, the intermediary (reflection point) sends it back to its origin, which (since the origin address has been spoofed) in this case is the victim's PC.
There are a collection of network protocols vulnerable to these types of attacks, but the most dangerous ones are those that can accidentally add an amplification factor to the whole process.
This means that attackers can send one corrupted packet to a reflection point, but the victim receives ten. In this case, the reflection DDoS attack comes with an amplification factor of 10.
RPC, NetBIOS and Sentinel services abused in a series of new reflection DDoS attacks
As Akamai is describing in its most recent threat market report, during the past seven months, attackers have turned to new mediums for carrying out reflection DDoS attacks.
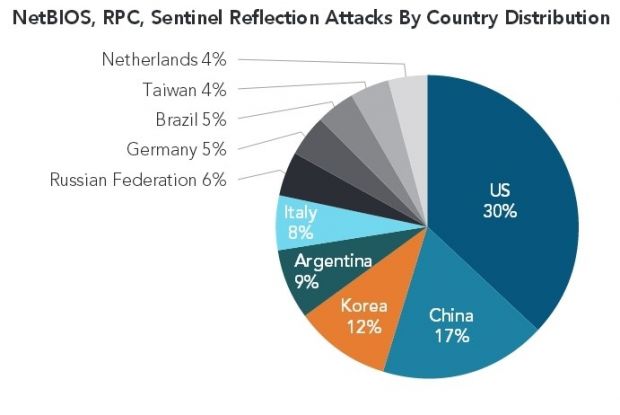
Ten reflection DDoS attacks have been observed in the past months using RPC, NetBIOS and Sentinel technologies, one of which managed to go over 100 Gbps (Gigabits per second). Akamai has also observed the presence of an amplification factor for all of the detected attacks.
NetBIOS attacks
NetBIOS is a protocol used in computer software to allow applications to talk to each other via LAN networks. The protocol was designed by IBM, adopted with early Windows versions, and works via the 137 port.
In the NetBIOS-based reflection DDoS attacks Akamai recorded, peak bandwidth never went above 15.7 Gbps, the amplification factor was between 2.56 and 3.85, and its main victims were targets in the gaming and Web hosting sector.
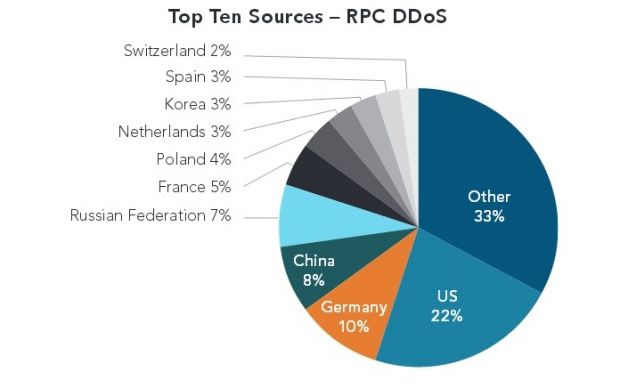
RPC attacks
The second type of reflection DDoS attacks detected by Akamai are the ones using RPC portmaps, a service that maps RPC service numbers to network port numbers.
These attacks peaked around 105.96 Gbps, had an amplification factor of 9.65, and the first that was observed dates back to August against a financial firm.
Because of their power, Akamai expects these attacks to become more popular in the upcoming months.
Sentinel attacks
IBM Sentinel license servers were also abused for reflective DDoS attacks. Sentinel servers are generally used in closed environments to manage user licenses for multi-user network setups.
If external UDP ports are left unattended for these services, attackers could use them to carry out DDoS campaigns.
Akamai observed reflection DDoS attacks using Sentinel servers coming out of the University of Stockholm, at a peak of 11.7 Gbps, with an amplification factor of 42.94.
The Akamai report serves to stand as a warning for network admins that leave external ports open, especially if those ports are handled by UDP-based protocols, known as regular mediums for carrying out reflection DDoS attacks.

 14 DAY TRIAL //
14 DAY TRIAL //