Sometimes crooks make mistakes when testing malware, and their soon-to-be-released product ends up in the hands of security researchers during its early stages of evolution, giving infosec professionals insight into how the threat gradually evolves.
The latest case of such an incident is HolyCrypt, a new ransomware variant detected by AVG security researcher Jakub Kroustek, who came across this new threat yesterday.
According to a source code breakdown compiled by Lawrence Abrams of Bleeping Computer, HolyCrypt is coded in a non-standard language for ransomware, Python, and was put together into an EXE file using the PyInstaller utility, previously also used to create the PWOBot keylogger and Bitcoin mining malware.
HolyCrypt coded in Python, uses AES encryption
HolyCrypt has a simple mode of operation. Once it infects victims, it encrypts their files using a static password. This is a simplistic mechanism, which security researchers like AVG's Kroustek, Emisoft's Fabian Wosar, or Michael Gillespie cracked in the past.
In the samples Kroustek detected, the password (key) used to start the AES encryption process was "test." Coupled with the fact that the ransomware targeted a very small number of file types for encryption, only twenty, this was an important clue that its author was still working on developing this threat.
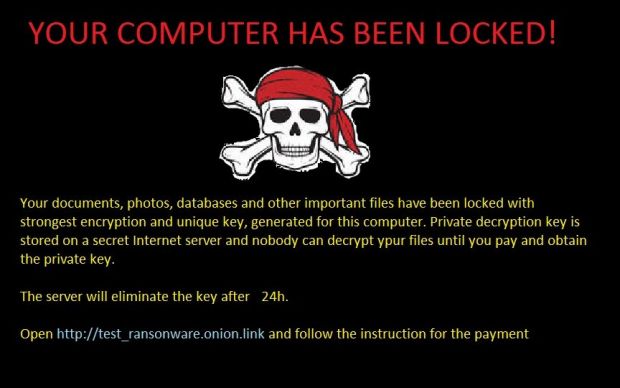
Furthermore, after the encryption ended, the ransomware also changed the user's desktop with a new wallpaper, embedded below.
As you can see for yourself, the link at the bottom of the wallpaper, where victims are supposed to go and pay the ransom, is a dummy link, also meaning that HolyCrypt's author has not fully deployed his entire crimeware infrastructures just yet.
HoylCrypt currently distributed as fake PDF files
As for the infection vector, Kroustek has told Softpedia that HolyCrypt's author is using the classic double extension trick, trying to hide the executable as a PDF file with names such ReportXYZ.pdf.exe.
"Although, I'm not sure why someone distributes such work-in-progress," the AVG researcher also adds.
Current versions of HolyCrypt prepend the "(encrypted)" string to all encrypted files. If you find your files locked, see the wallpaper below and the (encrypted) string in all your file names, then do a quick Google search for "HolyCrypt decrypter" and see if security researchers haven't cracked it in the meantime.

 14 DAY TRIAL //
14 DAY TRIAL //