A new Mirai variant was discovered in the wild, being used to launch a 54-hour DDoS attack against a US college.
Although researchers over at Incapsula spotted the attack as it happened, they're only just reporting on it. It seems that the attack started on February 28 and ran for 54 hours straight, targeting a US college, which is one of the company's customers.
The average traffic flow was of 30,000 requests per second (RPS), although it did peak at around 37,000 RPS, which is the most that the Mirai botnet has used thus far. In total, the attack generated over 2.8 billion requests.
The Mirai malware was discovered last August, and it has been used thus far in a number of DDoS attacks. Since the Mirai source code is publicly available, botnet herders began experimenting with new versions of the malware and, thus, created new, more powerful variants.
Researchers determined that the botnet used in last month's attack was powered by the Mirai botnet thanks to a number of signature factors, including header order, header values, and traffic sources. The pool of attacking devices included CCTV cameras, DVRs and routers, which are commonly used by Mirai.
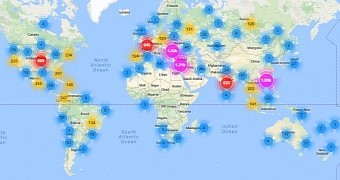
18% of Mirai bots are in the USA
Attack traffic originated from 9,793 IPs from all over the world, 70% of which were located in ten countries: USA, Israel, Taiwan, India, Turkey, Russia, Italy, Mexico, Colombia, and Bulgaria.
Once the initial attack ended, criminals began another one that lasted just about an hour and a half, and it was a lot tamer, with an average traffic flow of 15,000 requests per second.
Incapsula refused to name the college that was under Mirai attack and since they have so many clients, it's impossible to tell just which it was and what exactly the perpetrators were hoping to achieve with this campaign.
 14 DAY TRIAL //
14 DAY TRIAL //