Yonathan Klijnsma, Senior Threat Intelligence Analyst for Fox-IT, a Dutch security firm, discovered a new ransomware variant named Maktub Locker, which appears to be the work of a professional malware coding team.
His discovery was also noted by the ransomware experts from Bleeping Computer and later by security vendor Malwarebytes.
Crooks are spreading the Maktub Locker ransomware via spam campaigns, just like most of today's ransomware infections. The emails carrying the threat come attached with .scr executables that have icons allowing them to pose as PDF or TXT files.
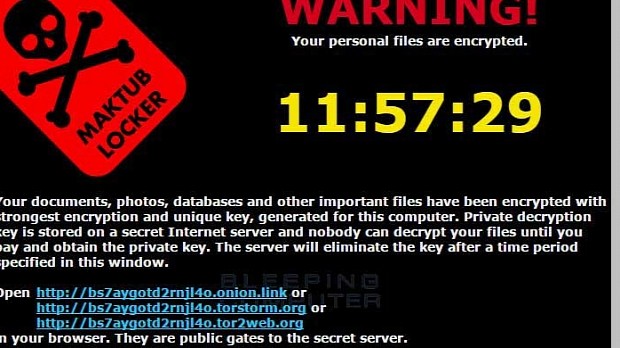
Maktub comes disguised as PDF or TXT files
When double-clicked, the SCR files launch fake apps that look like a PDF reader or a text editor, presenting the user with some "updated terms of service" but secretly encrypting their data behind their back.
Maktub, which means "it is written" (as in "it was always meant to happen") in Arabic, uses a strong AES-256 encryption algorithm to lock up the victim's files.
For each victim, the ransomware appends a different file extension, which makes it harder for users and security experts to detect which ransomware family has locked the data and search for decrypters.
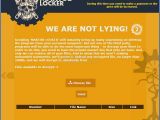
The only clue is Maktub's ransom payment site, hosted on the Dark Web via TOR, which uses a high-quality design that stands apart from all the drab and boring ransom payment websites used by competitors.
The ransom payment site has five pages, each with its own different coloring scheme, and a professional logo, stolen from US designer BlackHawk45LC's DeviantArt portfolio.
Ransom price can reach $1,600 after two weeks
Another difference is the six-step payments scale, which goes from 1.4 Bitcoin (~$600) in the first three days after the infection to 3.9 Bitcoin (~$1,650) after 15 days. This is above average when compared to most ransomware variants, which ask between 0.5 and 1 Bitcoin per infection, a price that only doubles after the first two-three days.
Maktub can work with or without a C&C server, and there's no known method of decrypting locked files at this point.
"Maktub Locker has clearly been developed by professionals," the Malwarebytes team writes. "The full product’s complexity suggests that it is the work of a team of people with different areas of expertise. From the packing operations to the website, everything is well-polished."
Another new piece of ransomware called 'MAKTUB LOCKER' currently spreading via mail. Requires no C2 coms to encrypt. pic.twitter.com/KSxS8pVK5a — Yonathan Klijnsma (@ydklijnsma) March 21, 2016
[FULLIMG=2[]
 14 DAY TRIAL //
14 DAY TRIAL //