FastPOS is the name of a new malware family discovered by Trend Micro that uses a unique approach to data exfiltration, focusing on getting the stolen credit card data as soon as possible to one of its servers.
Most POS (Point Of Sale) malware works by infecting a system and staying hidden, collecting data in a file and uploading it to its server at regular intervals.
The reasoning behind this approach is to take as little time as possible communicating with the malware's C&C (command and control) server, and by doing so, minimize the chances of getting spotted.
FastPOS doesn't care about this aspect, and Trend Micro says the malware sends any stolen data to the C&C server as soon as it can get its hands on it.
FastPOS also includes a keylogger
The malware itself is made of two modules: a keylogger and a memory scraper. The keylogger collects all keystrokes, from any window on the infected computer.
As soon as the user presses Enter, the data is sent to the C&C server, along with the name of the window from where it was collected. This module can be used for all sorts of bad things, not just stealing credit card details.
On the other hand, the second module, the RAM scraper, is aimed at credit card details alone. This module works inside the infected host's memory and will send any credit card details it finds at any particular point.
A real-time data verification process makes sure the stolen data is actually in the format of a credit card number before sending it to the C&C server.
FastPOS takes shotgun approach to infecting hosts
"FastPOS’s design sets it apart from other POS malware families," Trend Micro notes. "It appears to be designed to operate in situations where a large, enterprise-scale network may not be present: instead, it is designed for environments with a much smaller footprint."
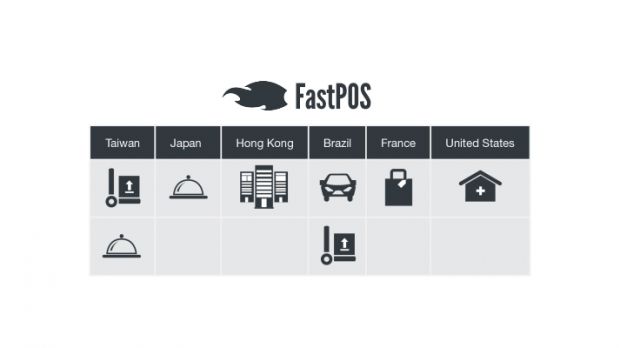
Researchers say they found FastPOS all over the world, and there doesn't appear to be a campaign aimed at a specific country, region, or industry. Until now, researchers have spotted FastPOS in the US, Brazil, France, Japan, Taiwan, and Hong Kong.
Trend Micro also said that the FastPOS infections they analyzed took place when the victims visited a real-time file sharing service, compromised medical sites talking about laser surgery, and after crooks brute-forced VNC connections and installed the malware by hand.
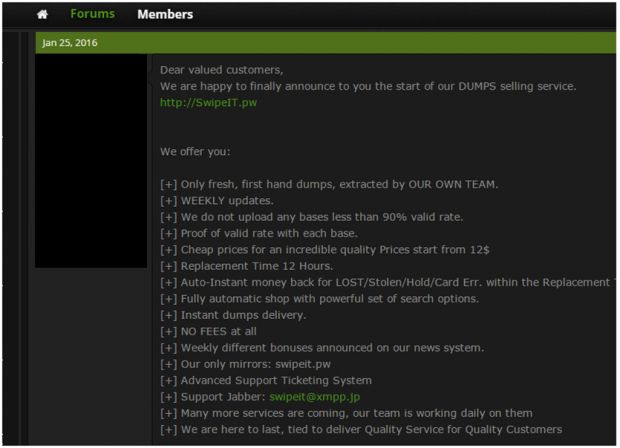
FastPOS on sale on an underground carding forum
Searching for the malware origins, Trend Micro experts found the crooks asking for support on various online forums, where they copy-pasted snippets of the malware's code asking for help.
Furthermore, the researcher even found an ad selling the malware on a forum hosting all sorts of stolen credit card details.
The researchers say the forum's IP is the same as the FastPOS C&C server IP, meaning the forum's operators are the ones behind the malware's distribution, and are probably using it to fuel their website with new "offerings."
For more details, check out Trend Micro's FastPOS (TSPY_FASTPOS.SMZTD) technical brief.

 14 DAY TRIAL //
14 DAY TRIAL //