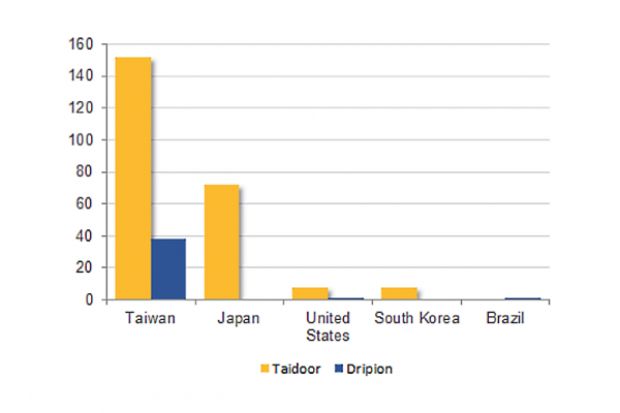
The Budminer cyber-espionage group is using a new backdoor trojan to target and spy on users in Taiwan, as well as the United States and Brazil, security researchers from Symantec have discovered.
The security vendor's staff came across this new trojan, called Dripion, in late August 2015, but in the meantime, they have been able to confirm earlier versions going back to November 2014, with some suspected strains dating back to November 2013.
Trojan is hosted on freely accessible online blogs
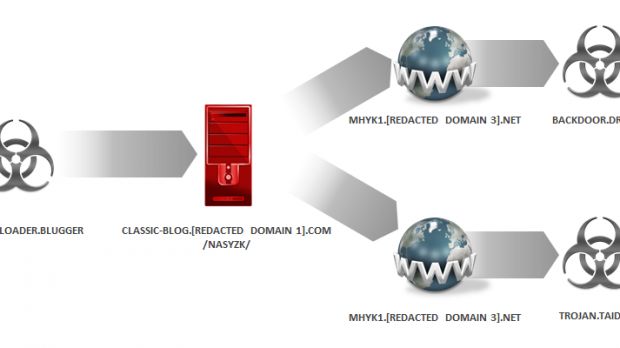
Symantec says that this new trojan is not distributed to victims directly, but through an intermediary trojan (a malware downloader) called Blugger, which connects to specific online blogs and retrieves the Dripion trojan from their filesystem.
Researchers aren't sure right now if these blogs have been hacked or have been set up by the Budminer group itself.
Once Dripion is downloaded and Blugger launches it into execution, the backdoor is activated and allows Budminer actors to download or upload files to the victim's computer, and then launch them into execution. The backdoor trojan's features are very limited but extremely effective.
Symantec discovered an interesting fact about Dripion, which uses URLs for its C&C servers that look like security products (mcfeesoft.com and nortonsoft.com).
Dripion is a failed attempt at evading detection
Things got interesting when researchers cross-referenced the Dripion campaign with their historic malware database, discovering that Blugger was used in live attacks only by one cyber-espionage group back in 2012. This is how Symantec attributed Dripion's deployment to the Budminer group.
The Budminer cyber-espionage actor was first discovered in 2012, when it used the very same tactic, employing the Blugger intermediary trojan to deliver another backdoor called Taidoor.
Just like in the Dripion campaign, most of the targets were in Taiwan and the US, but also in Japan and South Korea. Besides the shared MO, the Taidoor and Dripion campaigns also share some C&C servers.
From Symantec's analysis, it is clear that the Budminer group decided to create a new backdoor malware after their initial Taidoor trojan was unmasked and neutralized in Symantec's 2012 ousting.
Even if the organization managed to create a new trojan from scratch, by reusing some of its infrastructure and the same operational tactics, the group has failed to fool researchers, who have now updated their security software to detect their malware.
 14 DAY TRIAL //
14 DAY TRIAL //