A cyber-espionage campaign named Operation Groundbait has been targeting members of the Ukrainian government and the Russian-backed separatists with clever spear-phishing emails and a custom malware family.
While cyber-espionage campaigns are becoming more prevalent these days, this operation was somewhat peculiar because it targeted both sides of the Ukrainian separatist war.
Security firm ESET, who discovered the campaign, says it detected the group behind Operation Groundbait sending spear-phishing emails to members of the Ukrainian government, Ukrainian journalists, but mostly to separatist leaders in the self-declared Donetsk and Luhansk People’s Republics.
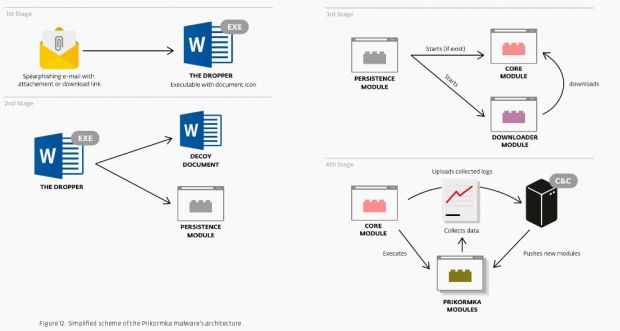
Most of the time, these emails contained fake news about the Ukraine separatist war. A malicious file attached to these emails, if downloaded and executed, would infect users with a powerful and modular malware, which ESET says the attackers can alter in real time with custom extensions, based on the victim they infected.
Fish for the phished: Fish bait price list file in a cyber-espionage campaign
The weirdest facet of this campaign was the presence of a file containing fishing bait information. This is extremely out of place in cyber-espionage attacks. The document is called prikormka.exe. Prikormka is Russian for "groundbait," hence the name of this operation and for the malware itself, Win32/Prikormka, classified as a backdoor trojan.
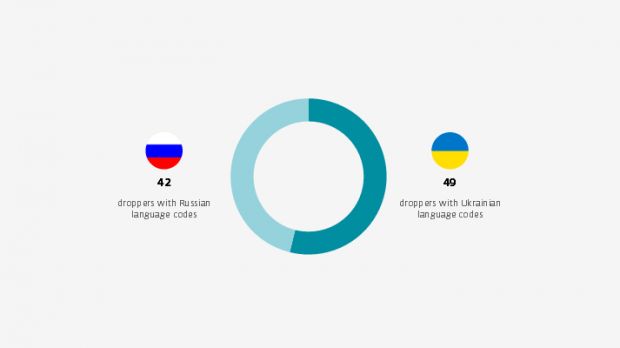
As for attribution for this wave of spear-phishing attacks, ESET says, "the attackers most likely operate from within Ukraine," mainly because of their focus on pro-separatist targets. Even if some Ukrainian officials and journalists were targeted, ESET says they might be false flags, to throw investigators off the group's real location.
Operation Groundbait comes five months after ESET discovered the BlackEnergy campaign, which attacked Ukraine's power grid infrastructure and eventually brought down electrical power for some Ukraine regions around Christmas. Additionally, another campaign aimed at Ukraine, named Operation Potao, was discovered in July 2015.
For more information, ESET has put together a 37-page report on Operation Groundbait, available as a free download.
 14 DAY TRIAL //
14 DAY TRIAL //