Security experts from Sucuri have discovered a new scamming method that combines the hijacking of e-commerce checkout pages and phishing sites.
In the past, crooks were seen hijacking sites and injecting malicious code into the checkout page on e-commerce portals to log the user's credit card details and transmit the data to a third-party site.
Additionally, security researchers have often noted how crooks used phishing pages that imitated the login or checkout pages for PayPal, payment sites or e-commerce portals to acquire the user's login credentials or credit card details.
Crooks combined two techniques to create a new attack scenario
It appears that a clever crook has come up with a way to combine the two tactics mentioned above and has created a new method for stealing user credit card details that is much harder to detect, by end users and Web security products alike.
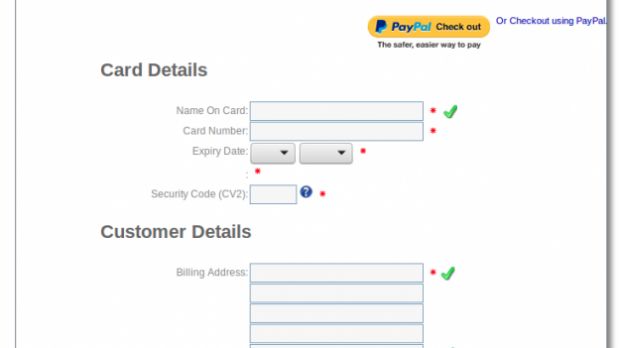
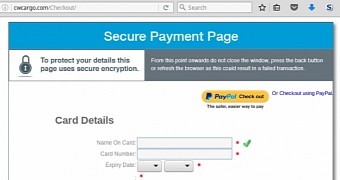
In the scenario seen and described by Sucuri, crooks are using malicious JavaScript code inserted on e-commerce portals to redirect the user to a checkout page under the attacker's control, on a different domain.
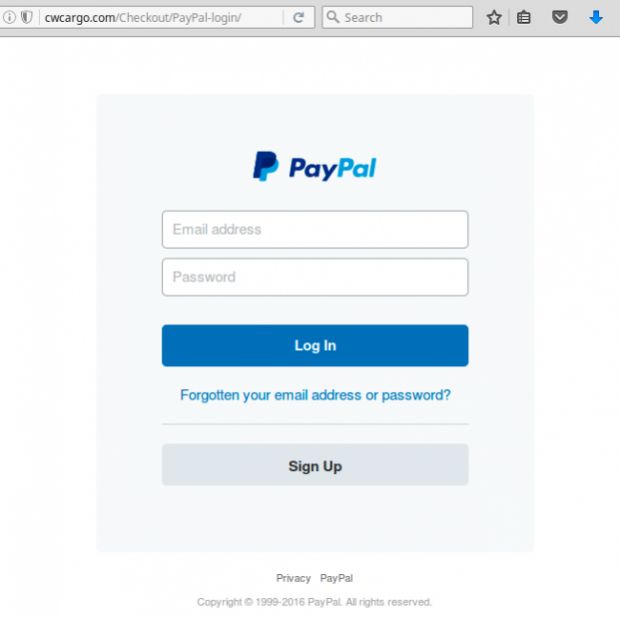
Once the user lands on this site, they are presented with a phishing page crafted to look like the original checkout page, but which will log their credit card details on the crook's server.
WooCommerce and Prestashop sites affected
Sucuri says that this new technique is relatively new, and until now, it has seen it used sparsely, on stores running WordPress WooCommerce and the Prestashop platforms.
Besides phishing pages for the checkout page, Sucuri says it detected a similar phishing page when the user tried to pay with PayPal. This page was hosted on the crook's domain as well.
The company says it only detected this campaign on a few websites, but the real number of affected sites could be much bigger because it is very hard to identify infected websites.
Detecting infected websites is extremely difficult
To scan a website for such a complex compromise, a security researcher would need to add products to the shopping cart and go through the ordering process until they reach the checkout page.
In most instances, this requires human testing, which is time-consuming. For automated security software, a security vendor needs to get permission from the scanned store to carry out such operations, because this may result in many abandoned orders that may ruin a site's internal statistics and analytics engines.
Users who land on these checkout phishing pages also tend to have their guard down. By this point, users have gone through most of the shopping process, logging in or setting up order details, and after spending so much time on the actual website, they forget to check the URL of the page where they enter the credit card details.
"Since victims are already in shopping mode and ready to enter their credit card number anyway, this phishing attempt may be more successful than classical tricks that distract victims from their tasks and ask to do something else instead," Sucuri's Denis Sinegubko explains.
 14 DAY TRIAL //
14 DAY TRIAL //