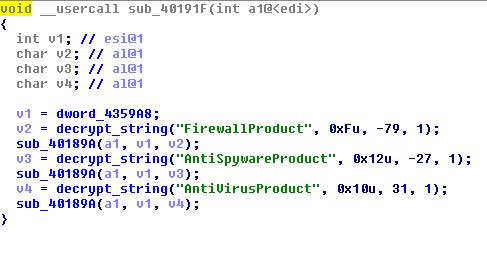
The Cerber ransomware has been around for quite a while, and many variants are out in the wild, but one in particular, which has been observed over the past few months, contains a function that allows it to avoid encrypting files from any security products on your device. This includes firewalls, antivirus software or antispyware products.
Security researchers over at Trend Micro have discovered the new variant as RANSOM_CERBER.F117AK, which they say first appeared online back on January 20. In the days since its discovery, researchers have simply scratched their heads, wondering why it would leave security tools running even after the Cerber ransomware locked the computer.
The regular behavior of malware such as Cerber is to do everything it can to avoid detection or to cripple the antivirus so as not to somehow get removed from the device it infected. Instead, this Cerber variant does the opposite and whitelists the security components on the device.
It goes out of its way to whitelist security files
"The built-in Windows Management Interface (WMI) is “the infrastructure for management data and operations on Windows-based operating systems.” In effect, it is a powerful tool used for (as the name implies) sharing system management information. This frequently includes software, including security products," reads the report from Trend Micro.
According to researchers, Cerber looks for three WMI classes, namely FirewallProduct, AntiVirusProduct, and AntiSpywareProduct. It then extracts the directories where these files are installed and adds them to a list of whitelisted folders, spared from encryption.
Furthermore, typical directories for software installation of any kind in Windows are part of the whitelist too, along with any executable files. "It appears that the attackers only want to be triply sure that security software it not encrypted," the researchers conclude.
Aside from these differences, this Cerber variant is pretty much just like any other else, asking for 1 BTC to return the files to their previous state, or 2 BTC if five days have passed.
 14 DAY TRIAL //
14 DAY TRIAL //