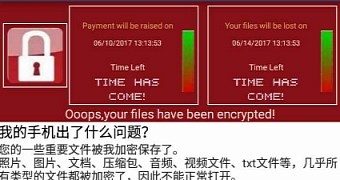
There's a new Android ransomware out there that is looking to scare people into thinking they've somehow been infected by WannaCry.
According to researchers from Qihoo 360, crooks are spreading the ransomware via Chinese gaming forums in an app that has been infected with the ransomware. Since the app tries to pass as a plugin for King of Glory, a very popular mobile game in China, there's been quite a few people affected.
This ransomware is quite odd because it asks users to pay a ransom of 40 Chinese Renminbi, which is about $6, via regular Chinese payment providers QQ, Alipay, or WeChat. The main reason other cybercriminals use Bitcoin or other crypto currencies is because those offer some sort of anonymity and law enforcement can't catch them as easily. With the roots the Chinese authorities have into technology firms in the country, coming up with the right names for all ransom payments wouldn't be too hard.
Full encryption delivered
On the other hand, while that part of the execution is downright risky for these attackers, the ransomware actually works as it's supposed to. The WannaCry lookalike encrypts files on the device, using AES encryption to lock them. The suffix appended to all encrypted files is a mix of Chinese and Latin characters, so it won't be difficult to figure out which were affected and which weren't.
However, due to limited resources on Android devices, the ransomware only encrypts files under 10KB in size, avoiding files that pertain to the Android OS, as well as files located in folders that include "android," "com," "DCIM," "download," or "miad" in their file path. Basically, this ransomware, which has been dubbed WannaLocker by security firm Avast, only encrypts files on the external storage of the smartphone.
 14 DAY TRIAL //
14 DAY TRIAL //