A known malware family that targeted many financial institutes in the past has suffered a significant change that has allowed it to become boot-persistent and hide in a hard drive's VBR (Volume Boot Record).
The malware family in question is called Nemesis by security analysts from FireEye, who've seen it in the past targeting banks, credit unions, ATMs, and financial transaction processing and financial business services companies.
FireEye has attributed this threat to a criminal group known only as FIN1, whom they assume to be from Russia or a Russian-speaking country, based on clues left behind in their tools.
In past cases, when FireEye analyzed FIN1's malware, most of the times, they came across different versions of the Nemesis family. This malware can perform a lot of actions, such as hidden file transfers, screen capturing, keystroke logging, process injection, process manipulation, and even task scheduling for delayed effects.
Nemesis malware now comes with boot persistence
According to a recently concluded analysis of one of the newly detected versions of the Nemesis malware, in early 2015, FIN1 updated their code by adding bootkit capabilities.
Bootkit capabilities allow a virus to infect computer code that's not part of the operating system itself. This code governs hardware activities, and in Nemesis' case, it controls how the computer boots up.
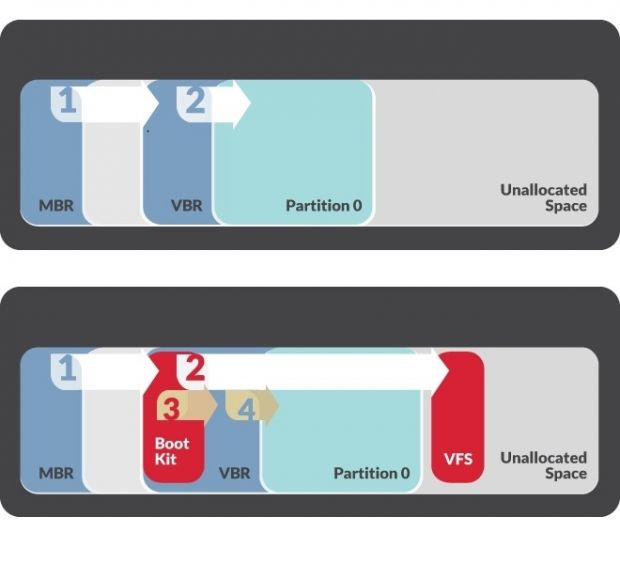
For Windows PCs, in a normal boot, the computer reads data from a hard drive's MBR (Master Boot Record). Here, it learns about the hard drive partitions, and the primary partitions it needs to load for the operating system to start. From here on out, the boot process moves to each partitions MBR-like structure, called the VBR (Volume Boot Record). The VBR provides more in-depth details about each partition.
FIN1 has modified Nemesis with a module that they call BOOTRASH, which, during a computer's infection process, rewrites some of the normal boot process and places itself in the VBR.
Nemesis hides key components in a hard drive's unallocated space
BOOTRASH sets up a hidden custom virtual file system (VFS), where it stores important Nemesis components. This VHS is stored in a hard drive's unallocated space.
During a computer's boot, the BOOTRASH module prevents the normal boot operations from running until its malicious code is executed, code that takes the Nemesis components stored in the VHS and injects them into the Windows kernel.
Security researchers have observed versions of BOOTRASH targeting both 32- and 64-bit architectures. Because of this newly added bootkit component, reinstalling the operating system won't remove the Nemesis malware.
"System administrators should perform a complete physical wipe of any systems compromised with a bootkit and then reload the operating system," FireEye recommends.
This is not the first malware family with boot persistence ever observed. In the past, security researchers also detected threats like ROCKBOOT, KINS, TDL4 (Olmarik), Rovnix, Necurs, and Carberp. The ones that targeted financial institutions were Carberp and KINS, both highly efficient banking trojans. Boot persistent malware is not common, mainly because it is very complex and requires advanced computer knowledge to properly implement without crashing a victim's computer.

 14 DAY TRIAL //
14 DAY TRIAL //