Security researchers from Avast decided to take a closer look at the Android apps of several online retailers, and to nobody's surprise, managed to discover a few vulnerabilities.
According to their research, the Target Android app comes with an API (Application Program Interface) that the developers failed to properly protect.
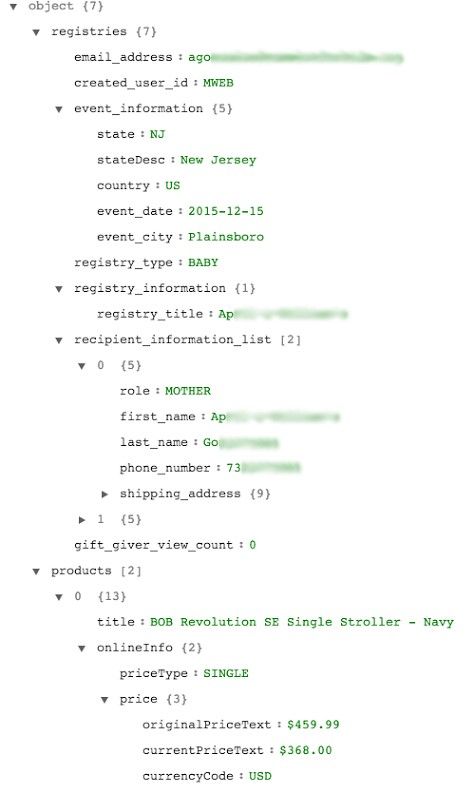
The API works by receiving queries (via HTTP requests) from a user's phone and then sending the response as a JSON file. This file is read by the app, the desired information extracted, and then displayed on the screen.
Unprotected Target API reveals customers' wishlists
Many other services like Twitter, Facebook, or Google use APIs. The difference between them and Target is that Target forgot to protect the API by authenticating users who can query for information.
Since the Target app handles lots of private information, this is a serious security lapse, which the Avast researchers exploited to gain access to information about 5,000 Target users.
According to the researchers, just by figuring out how Target assigns IDs to each user, an attacker could blindly query the API for data on random IDs, and build himself a database of Target users.
The Target API spews information about users such as their real names, email addresses, shipping addresses, phone numbers, and their wishlists.
Attackers can harvest the API for personal details
An attacker could easily scrape the Target API and harvest information about target users en-mass, and then use it in spam campaigns. A similar issue was also discovered in Facebook’s GraphQL last summer when a British developer managed to blindly harvest information on thousands of Facebook users by testing random phone numbers.
"Since the news broke, Target has suspended elements of the app while developers investigate," an Avast spokesperson told Softpedia.
Outside the Target app, Avast researchers also tested applications from other retailers like Home Depot, J.C. Penney, Macy’s, Safeway, Walgreens and Walmart. Avast says it found issues in other apps, which it plans to disclose at another time.
As a side note, Avast said that during their investigation, by far, the Walgreens Android app requested the highest number of unnecessary permissions of all the tested apps, with the Home Depot app coming in a close second.
 14 DAY TRIAL //
14 DAY TRIAL //