Russian security vendor Kaspersky Lab, who assisted with the official police investigation, has confirmed today that the cyber-crime syndicate that developed the Lurk banking trojan was also the team that developed the Angler exploit kit (EK), the world's most popular crimeware kit at the time of its demise.
At the end of May, Russian authorities announced they arrested 50 people, detaining 18, for their involvement in the distribution of the Lurk banking trojan, which was used to steal more than $45 million (3 billion rubles) from Russian banks and other financial companies since 2011.
Lurk had a huge impact on banking software worldwide
The trojan, which initially targeted RBS (Remote Banking Software) used in Russian banks, had a huge impact on the financial market in Russia and all over the globe.
Two years after it appeared on the scene, along with other RBS-targeting malware like the one developed by the Carberp gang, banks and RBS software vendors introduced several security measures in the money transferring process worldwide.
RBS software vendors stopped offering free demos of their product while banks added two-step verification and off-site authentication codes.
Angler EK appeared when profits from Lurk died down
These changes happened in 2013, about the same time Kaspersky and other security vendors can track down the first versions of Angler.
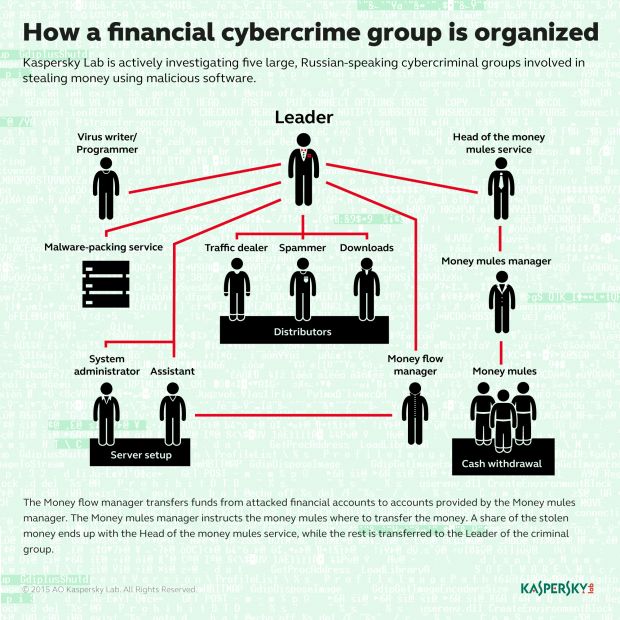
Kaspersky's experts put forward the theory that the Lurk gang, which was operating a huge crew of malware developers, money mules, spammers, and others, had to find another stream of revenue to pay their employees.
As such, the team decided to open a part of their infrastructure to other criminal groups. Until that moment, the Lurk gang kept the tools it developed only for its own operations.
What they decided to make available for rent was their toolkit used to serve malware via drive-by downloads. This toolkit was later named Angler by the security firms that analyzed it.
Angler is a complex Web-based software package that uses scripts on special servers called "gates" to identify users running vulnerable software.
These scripts, once they detect a vulnerable user, redirect them to the final Angler landing page, where the main Angler process uses JavaScript, Flash or Java objects to deliver exploits to the user's browser or their underlying operating system.
Using this method, Angler will then be able to force-feed a victim a particular payload. The Lurk gang developed this system to deliver their banking trojan to computers running RBS software, but after 2013, other crooks took advantage to introduce all sorts of malware.
Angler was the world's biggest EK service
In the past three years, Angler became the top dog on the EK market and was used to deliver ransomware, banking trojans, adware, and whatever you can think of. Angler's most biggest campaigns often distributed TeslaCrypt (ransomware), CryptXXX (ransomware), or Neverquest (banking trojan).
"The Lurk gang did not make [...] blunders. Yet mistakes, seemingly insignificant and rare, still occurred. And when they did, we caught them," the Kaspersky team wrote today, revealing their huge role in unmasking this criminal gang.
All these mistakes led to the group getting arrested around the end of May. By mid-June, the Angler exploit kit had seemingly disappeared from the EK market. Even if there was no official announcement from Russian police, most people suspected that the Lurk arrests had something to do with it.
Today, Kaspersky has made it official. The company has also published a must-read account on how it hunted down the Lurk gang.
 14 DAY TRIAL //
14 DAY TRIAL //