A vast online fraud operation was dismantled by the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) with extensive help from privately-held companies such as Google, Microsoft, WhiteOps, ESET, Trend Micro, and Malwarebytes.
The U.S. Department of Justice (DoJ) also unsealed a 13-count indictment today that charges eight individuals for running the massive digital advertising fraud scheme.
At the moment only three of the defendants have been apprehended by international law enforcement agencies (i.e., Sergey Ovsyannikov, Aleksandr Zhukov, and Yevgeniy Timchenko), while the other five (i.e., Denis Avdeev, Dmitry Novikov, Boris Timokhin, Mikhail Andreev, and Aleksandr Isaev) are still at large and are currently wanted.
"Also unsealed today in federal court in Brooklyn were seizure warrants authorizing the FBI to take control of 31 internet domains, and search warrants authorizing the FBI to take information from 89 computer servers, that were all part of the infrastructure for botnets engaged in digital advertising fraud activity," says DoJ's press release.
The group behind the ad fraud network used two schemes, the first one dubbed Methbot which used 1,900 datacenter servers to load the ads bought from advertising networks on fake websites hosted on more than 5,000 domains.
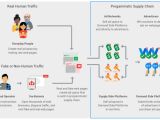
The defendants also employed data center servers and roughly 650K IP addresses to mimic residential computers, together with automated programs to fake human interaction with the ads to prevent the advertisers from detecting the fake ad traffic.
The crooks behind the two ad fraud schemes collected more than $36 million in total
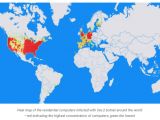
The second digital ad fraud scheme named 3ve employed two botnets, dubbed Kovter and Boaxxe according to US-CERT, of roughly 1.7 million malware-infected computers they controlled to visit fabricated web pages in the background loaded with ads.
Also, the group wielded the Boaxxe and Kovter botnets to open thousands of web browsers, disguising their traffic and visiting both real and fake web pages to create fraudulent ad inventory designed to trick advertisers that real users see their ads, costing them millions in ad revenue.
With the help of the two online ad fraud schemes it operated, the group was able to fake billions of ad views and collected more than $36 million in total from ads that were never seen by human eyes.
"Finally, the United States, with the assistance of its foreign partners, executed seizure warrants for multiple international bank accounts in Switzerland and elsewhere that were associated with the schemes," concludes the DoJ press release.

 14 DAY TRIAL //
14 DAY TRIAL //