Mozilla security engineer April King released a project called Observatory, a free website security scanning utility, similar to SSL Labs and High-Tech Bridge's scanning service.
The service, working on top of a Python codebase made available on GitHub, has been under development for months and was approved for a public launch only yesterday.
Observatory is aimed at developers, system administrators, and security professionals that want to configure sites to use modern security protocols.
Service uses A to F scores to grade website security
Observatory scans for the presence of basic security features and then gives out a grade from 0 to 130, which is then converted into an A to F score.
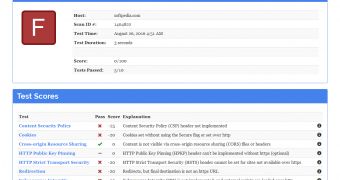
In its current form, the service scans for the following: [1] Content Security Policy (CSP) status, [2] cookie files using Secure flag, [3] Cross-Origin Resource Sharing (CORS) status, [4] HTTP Public Key Pinning (HPKP) status, [5] HTTP Strict Transport Security (HSTS) status, [6] the presence of an automatic redirection from HTTP to HTTPS, [7] Subresource Integrity (SRI) status, [8] X-Content-Type-Options status, [9] X-Frame-Options (XFO) status, and [10] X-XSS-Protection status.
All basic security recommendations, albeit extremely hard to implement, a reason why many websites still don't use them.
Over 91% of current websites fail Observatory's tests
According to King, who performed automatic scans of over 1.3 million websites, over 91 percent of modern-day websites fail Observatory's tests.
"When nine out of 10 websites receive a failing grade, it’s clear that this is a problem for everyone. And by “everyone”, I’m including Mozilla — among our thousands of sites, a great deal of them fail to pass," King wrote yesterday, revealing that Observatory was developed to help Mozilla tests their own domains first.
| Year | Technology | Attack Vector | Adoption† |
|---|---|---|---|
| 1995 | Secure HTTP (HTTPS) | Man-in-the-middle Network eavesdropping |
29.6% |
| 1997 | Secure Cookies | Network eavesdropping | 1.88% |
| 2008 | X-Content-Type-Options | MIME type confusion | 6.19% |
| 2009 - 2011 | HttpOnly Cookies | Cross-site scripting (XSS) Session theft |
1.88% |
| 2009 - 2011 | X-Frame-Options | Clickjacking | 6.83% |
| 2010 | X-XSS-Protection | Cross-site scripting | 5.03% |
| 2010 - 2015 | Content Security Policy | Cross-site scripting | .012% |
| 2012 | HTTP Strict Transport Security | Man-in-the-middle Network eavesdropping |
1.75% |
| 2013 - 2015 | HTTP Public Key Pinning | Certificate misissuance | .414% |
| 2014 | HSTS Preloading | Man-in-the-middle | .158% |
| 2014 - 2016 | Subresource Integrity | Content Delivery Network (CDN) compromise | .015% |
| 2015 - 2016 | SameSite Cookies | Cross-site reference forgery (CSRF) | N/A |
| 2015 - 2016 | Cookie Prefixes | Cookie overrides by untrusted sources | N/A |
 14 DAY TRIAL //
14 DAY TRIAL //