A group of state-sponsored hackers supposedly operating out of India, based on current evidence, have been targeting thousands of individuals and organizations around the globe for almost six years.
According to evidence gathered by infosec researchers from the Forcepoint Security Labs, the group, which they dubbed Monsoon during the initial phase of their research, turned out to be the same APT also known under three different names, discovered by three other companies.
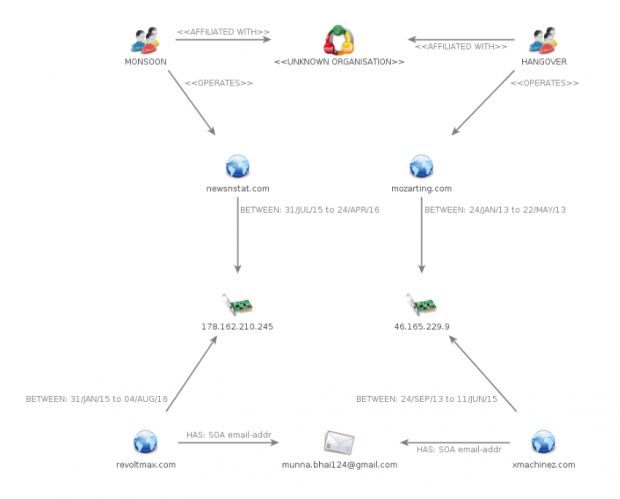
Monsoon is actually the Patchwork APT, as named by Cymmetria last month; Dropping Elephant, as called by Kaspersky Lab last month; and Operation Hangover, the codename it received from Blue Coat in 2013.
Monsoon is connected to Operation Hangover attacks
The last APT name is a connection that both Cymmetria and Kaspersky failed to make in their initial reports, but Forcepoint says that, after an analysis of the domain names and server infrastructure used in the attacks, it managed to find some overlaps between their Monsoon report and Operation Hangover.
Looking deeper at the collected data, Forcepoint identified not only an infrastructure overlap but also the usage of similar TTPs (Techniques, Tactics, and Procedures) and the targeting of same individuals.
Monsoon, Patchwork, Dropping Elephant, Operation Hangover, or whatever you want to call it, seems to have operated in cycles, with the latest one starting back to December 2015, the same start date reported by Forcepoint, Kasperksy, and Cymmetria in all their research.
Spear-phishing campaigns revolved around military topics
The name of the malware detected in these attacks differs from company to company, but the crooks used spear-phishing emails to deliver malicious Office files, which, in turn, infected the victims, mainly with a backdoor trojan.
The theme of the spear-phishing emails was the same in most cases, revolving around current newsworthy topics, but most of the times around the Chinese military as well as the military and defense fields in general.
The malicious Office files used primarily three vulnerabilities to deliver the malware: CVE-2012-0158, CVE-2014-6352, and CVE-2015-1641.
The various types of malware these exploits reported to a crude C&C server infrastructure hosted using non-traditional services such as RSS feeds, forums, and GitHub accounts. In its report, Cymmetria called the group non-sophisticated and said it used malware code copy-pasted from online sources.
Some of the evidence points to India
Overall, as Kaspersky reported, the group targeted a large number of people, over 6,300, and located in over 110 countries.
Forcepoint stayed away in its report from pointing the finger at India, just like Cymmetria and Kaspersky, but it did leave enough clues for readers to reach this conclusion.
These include domain names registered to an individual living in India and the repeated targeting of India's neighbors. Three years ago, Blue Coat attributed Operation Hangover to an Indian threat actor. For more details, feel free to consult Forcepoint's Monsoon's report.

 14 DAY TRIAL //
14 DAY TRIAL //