Security specialists from iSIGHT Partners have identified a new malware family targeting POS (Point of Sale) devices, one that, due to its very high level of complexity, they are characterizing as a criminal malware framework.
The malware was named ModPOS, Mod standing for modular, representing its architecture, which relies on countless modules to add the malicious functionality it needs.
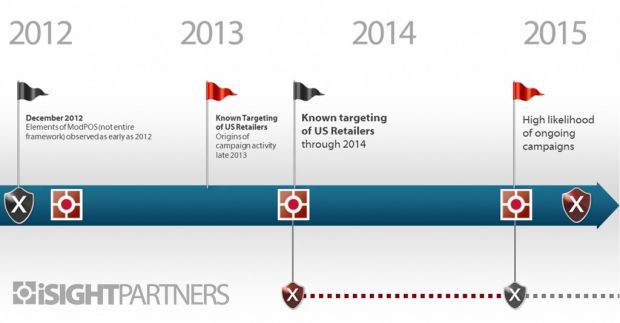
According to iSIGHT, ModPOS has remained undetected for at least three years, its researchers having observed elements of its framework going back to 2012. Real-world attacks had first been observed against US retailers in late 2013 and continued all through 2014 and 2015.
ModPOS behaves differently on each infected target
The analysis was difficult because the technical details were different for each target, something made possible due to ModPOS' versatile and modular structure.
ModPOS' main modules are Uploader/Downloader, Keylogger, and POS Scrapper. These three are supposed to provide basic RAM scrapping, communication, and exfiltration functionality.
If credit/debit card or another type of data sent from an initially infected device is deemed valuable, the malware's C&C server will then tell the downloader to fetch other modules, based on the infected system's technical makeup.
Other modules provide functionality for querying about local processes and system settings, viewing and inspecting the local network, and for gathering username and password information for local and domain accounts.
Currently undetected by security software solutions
All modules are packed kernel drivers that also utilize obfuscation and encryption to evade security software. iSIGHT reports that only the Uploader/Downloader module is detected by antivirus solutions, but by only one vendor, which marks it with a low-security risk.
As for attribution, iSIGHT's researchers claim that current samples have led them back to Eastern European servers.
"In a nutshell, this is not your daddy’s run-of-the-mill cyber crime malware," says iSIGHT's Stephen Ward. "The actors behind the ModPOS software have exhibited a very professional level of software development proficiency, creating a complex, highly functional and modular code base that places a very heavy emphasis on obfuscation and persistence."
The entire report describing ModPOS' functionality can be downloaded upon request from iSIGHT's homepage.

 14 DAY TRIAL //
14 DAY TRIAL //