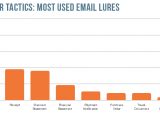
Attackers have always preyed on human behavior to distribute malware. Either they target persons with lower technical skills or gullible users, in the vast majority of cases, it's always our fault when we get infected with malware.
In its annual Human Factor 2016 report, security firm Proofpoint detailed a few trends it noticed during the past year in terms of malware distribution across different platforms.
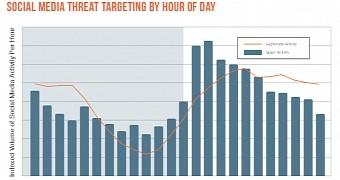
Attackers add social media campaigns to their distribution methods
"Attackers moved from technical exploits to human exploitation in 2015," said Kevin Epstein, Vice President of Threat Operations for Proofpoint. "People’s natural curiosity and gullibility is [sic] now targeted at an unprecedented scale."
During the past year, attackers ditched overly complicated technical exploits and switched back to running high-volume campaigns, mainly through email, but also through social media and infected mobile apps.
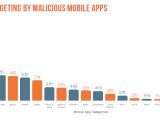
Proofpoint says that, this past year alone, unsuspecting victims downloaded more than two billion mobile apps infected with data-stealing malware.
Even worse, Proofpoint adds that, in the case of 12,000 of these apps, they were hosted on authorized Android app stores, which users generally visited for the sole purpose of staying away from malware.
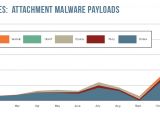
As for other threats, the company is also reporting that, in 74% of all email spam, the malicious payload was one of the multiple variants of the Dridex banking trojan.
Campaigns timed to arrive in the morning
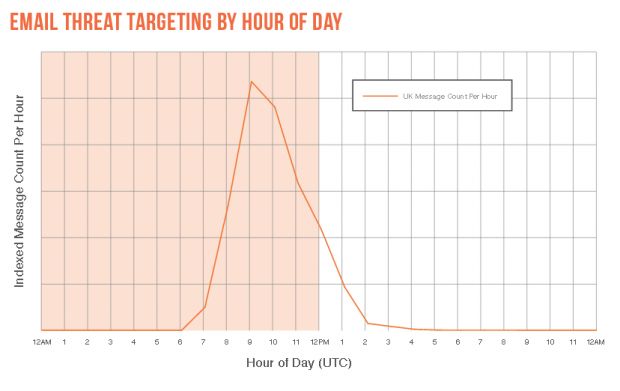
To make sure their malicious payloads are opened, attackers also timed emails spam campaigns to arrive on the target's local timezone, between 9 and 10 AM.
Additionally, 74% of all links included in malicious email pointed to phishing sites, not downloadable malware. Most of the times, these links led to file-sharing sites like Google Drive and Dropbox.
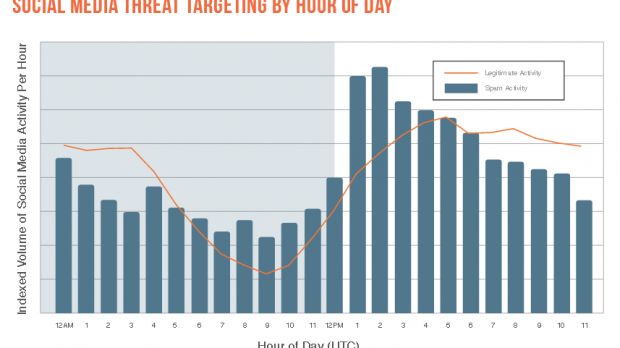
On social media, the percentage of phishing links is even bigger, ten times higher than links to downloadable malware.
Further, Proofpoint also saw a spike in CEO fraud (or Business Email Compromise) scams. Attackers focused phishing campaigns and social engineering attacks on one or two persons inside a company, trying to trick them into wiring money to wrong accounts.
Since we read our fair share of security reports, most of Proofpoint's findings are in keeping with other studies from other security vendors.
 14 DAY TRIAL //
14 DAY TRIAL //