Back in September, Kaspersky experts revealed that the infamous threat known as Flame had at least three more brothers: SP, SPE and IP. Initially, the researchers believed that SPE – dubbed miniFlame – was a module of Flame, but their investigation has unveiled that it’s actually a unique standalone malware.
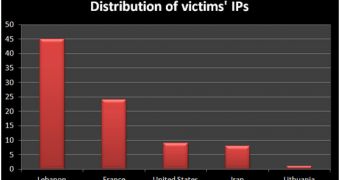
miniFlame is not as widespread as its bigger brother, the number of recorded victims being 100 times less. However, experts have found that, although the number of targets is small, the victims are most likely high-profile organizations.
The malware’s main purpose is to act as a backdoor on infected systems to allow its mastermind to take complete control of a device.
SPE was developed at around the same time as Flame and Gauss (2010-2011), which might explain why both pieces of malware used miniFlame as a module.
The infection vector is unknown, but unlike Gauss, miniFlame implements a full client/server backdoor which allows its master to directly access the affected system.
Curiously, Flame’s command and control server code doesn’t contain a module to control SPE clients, which might mean that the malicious element has (or had) its own dedicated servers.
Another noteworthy aspect is that the other brother, SP, might actually be an earlier version of SPE.
The discovery of miniFlame not only reinforces the theory of a connection between the teams that developed Gauss and Flame, but it also shows that the cybercriminals might have planned out their operations to take place in waves.
“First wave: infect as many potentially interesting victims as possible. Secondly, data is collected from the victims, allowing the attackers to profile them and find the most interesting targets. Finally, for these ‘select’ targets, a specialized spy tool such as SPE/miniFlame is deployed to conduct surveillance/monitoring,” Kaspersky researchers said.
The complete technical paper on miniFlame is available here.
 14 DAY TRIAL //
14 DAY TRIAL //