SharePoint, one of the tools included with Microsoft Office's server suite, has been patched to protect users from a persistent XSS (cross-site scripting) flaw which could expose their private information.
The vulnerability (CVE-2015-2522) was discovered by security researchers at FortiNet's FortiGuard Labs, and affects SharePoint 2013 15.0.4571.1502 and earlier versions.
SharePoint is a web application platform developed by Microsoft, which combines various business management-related features into one single toolset, freeing system admins from having to deal with numerous software platforms at a time.
In most real-world scenarios, SharePoint servers are deployed in closed enterprise networks, serving as intranets for mid-to-large businesses, being one of Microsoft's best enterprise products to date, providing content management, document management, personal cloud, social networking, search, business intelligence, and workflow management features.
Improperly sanitized user input leads to XSS flaw exploitation
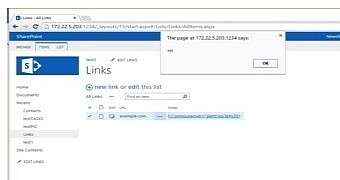
According to FortiNet's researchers, an attacker can take advantage of this recently discovered vulnerability by entering malicious code in a few input fields improperly sanitized by Microsoft's SharePoint platform.
These fields are for recording notes, keywords, and comments, and anyone with access to them can store a persistent XSS flaw on the SharePoint server, which can then be served to unsuspecting users accessing that particular page where the XSS was recorded on.
Successful exploitation of this vulnerability allows attackers to force victims to download and execute malicious code from controlled sources, redirect the user's browser to another page serving malicious content, or make a fake authentication popup appear and ask for the user's login details.
The vulnerability goes hand in hand with exploit kits
Researchers also claim that attackers can also expose and steal sensitive information stored in authentication cookies or from user agent strings. This data, as the FortiNet staff points out, can then be used in correlation with exploit kits and redirect users to an "adequate" malware payload.
Additionally, because SharePoint is often used together with Windows Active Directory servers, attackers can also gain access to shared enterprise login credentials, and by doing so, gain access to the company's entire suite of services.
Microsoft has patched this vulnerability (MS15-099) with one of its security update release trains.
 14 DAY TRIAL //
14 DAY TRIAL // 