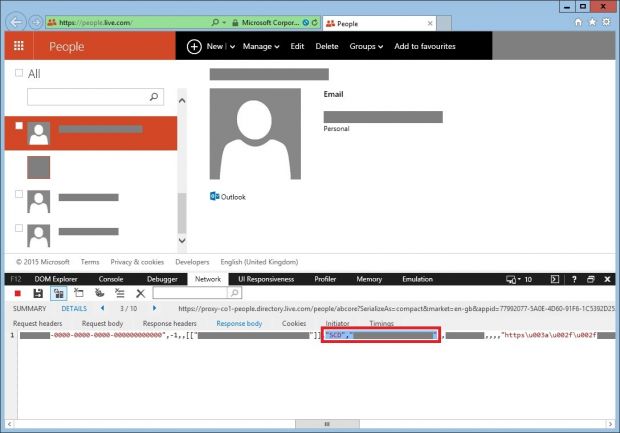
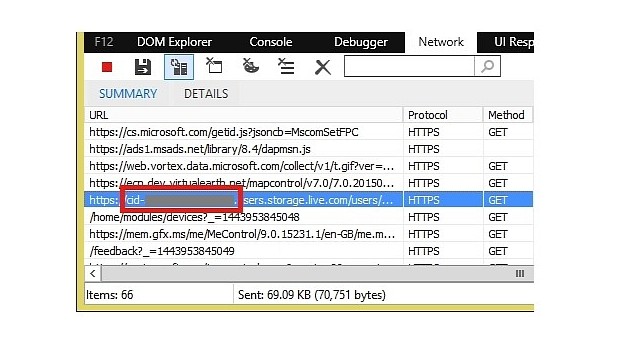
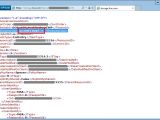
A Chinese developer only known under the name of ramen-hero has pointed out the fact that Microsoft leaks the CID identifier when performing DNS queries in clear text, a special piece of information that attackers could use to identify traffic coming from a specific person/account.
The problem can be found in Outlook.com, OneDrive, and Microsoft's account page, where, despite the presence of an HTTPS connection, the CID associated with each account is incorporated in the URL.
As ramen-hero explains, an attacker or government agency monitoring DNS traffic can easily detect connections coming from one person based on their CID.
The problem is that this CID is unique to each user account and allows attackers to connect various Microsoft services to users who would like to keep their privacy for various reasons.
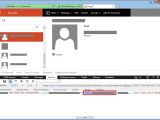
The CID can reveal a person's account picture, show the display name attached to each account, and the date the account was created.
Additionally, using some code trickery, the CID can also reveal the person's location via a legacy Calendar app version, which publicly displays the CID and weather forecasts. If the user receives weather information in their Calendar app, then the weather location identifier can be used reliably to detect the user's day-to-day location.
The CID is also leaked in TOR traffic
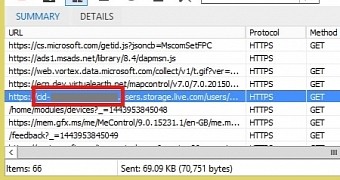
Expanding on ramen-hero's research, other users have also pointed out that, because the CID is part of the domain name in various communications, attackers don't necessarily need to monitor DNS traffic.
The CID is also leaked during TLS handshakes and even in Tor traffic if the exit node is monitored.
"If you have linked your Microsoft account with your Skype account," says ramen-hero, "anyone who knows your Microsoft account’s main alias can also obtain your CID using the People app."
This opens the door to serious privacy problems since attackers and those pesky government agencies can now interconnect Web traffic to single individuals and monitor them.
What Microsoft should do in this situation is not add the CID in clear text inside URLs, and also protect Web and API queries against a user's CID revealing personal and identifiable information.
 14 DAY TRIAL //
14 DAY TRIAL //