Microsoft's September Patch Tuesday security update includes a fix for a critical problem reported by enSilo researchers that affects hundreds of Windows applications, including Microsoft's own line of products.
In infosec circles, the vulnerability has been affectionately named Captain Hook, based on the name of the presentation given by enSilo researchers at this year's Black Hat USA security conference.
Vulnerability resides in little-known Microsoft component
The Captain Hook research paper detailed a vulnerability in Detours, a hooking engine created by Microsoft that allows third-party applications to tap into core OS API functions.
The research focused on the security problems the Detours vulnerability introduces in antivirus engines, but other applications also use the Detours engine, including Microsoft's Office suite.
The fourteen-year-old Detours engine is used for app virtualization, sandboxing, and performance monitoring. Exploiting the flaw discovered by enSilo would allow malicious actors to evade anti-malware detection systems and execute malicious code on the device.
Flaw fixed via KB3118268, kinda
enSilo said that Microsoft patched this issue in KB3118268, an Office update labeled as "Critical," included in security bulletin MS16-107. While the update fixes Office alone, enSilo says that Microsoft worked behind the scenes to update the Detours engine.
Researchers say they informed Microsoft of the vulnerability over six months ago, and Microsoft has notified all the 100+ ISVs (independent software vendors) that purchased a license for the Detours engine.
In theory, all apps that deploy Detours should have integrated the patched hooking engine, and issued updates. In reality, most apps are probably vulnerable, and will remain so for months, if not years.
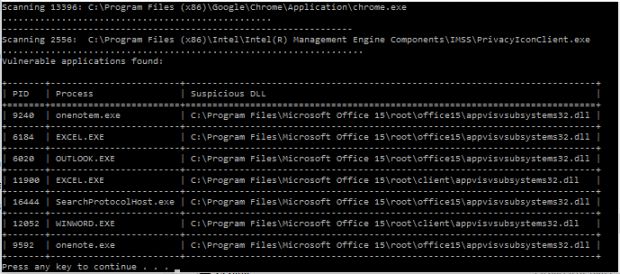
The enSilo team has created an app called FindADetour, which they've open-sourced on GitHub.
Users are encouraged to start different applications, and then run the enSilo app. FindADetour will scan all running processes, identify apps that use the Detours engine, and attempt to exploit the vulnerability. The enSilo scanner then lists all vulnerable apps in a Windows command terminal, like in the image below.

 14 DAY TRIAL //
14 DAY TRIAL //