Yesterday, The Windows Defender Advanced Threat Hunting team revealed the existence of a new APT (Advanced Persistent Threat) group that has been targeting countries in Southeast Asia since 2009.
Dubbed Platinum, following Microsoft's tradition of naming APT groups after chemical elements, the group distinguishes itself among similar cyber-espionage groups thanks to a novel technique called hotpatching.
What is Windows hotpatching?
Hotpatching allows Microsoft to issue updates that tap into active processes and upgrade applications or the operating system without having to reboot the computer.
The feature was introduced in Windows Server 2003 and later removed in Windows 8, after Microsoft realized its error.
No attacks have ever been recorded using this technique until now, but security researchers have proven its lethal capabilities at various security conferences.
Hotpatching used to avoid antivirus detection, push backdoors
According to a comprehensive report released on the Platinum APT, Microsoft says the group used the hotpatching technique to install and later conceal backdoors and other malware from a victim's antivirus solutions.
Due to its nature and design, hotpatching is not kept under a close eye by security products. This allowed the Platinum APT to push malicious updates to infected targets, neutering various features and allowing threat actors access to sensitive computers.
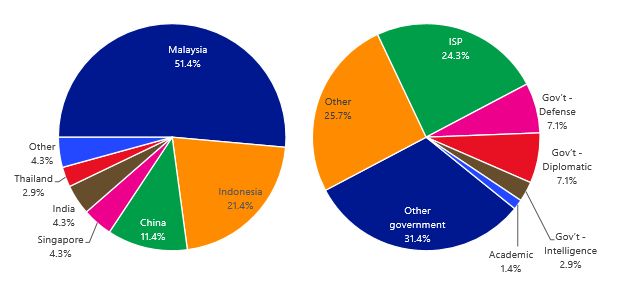
Microsoft says that it detected the Platinum group using this technique to install the Dipsing, Adbupd and JPIN backdoors on networks belonging to governmental organizations, defense institutes, intelligence agencies, and telecommunication providers.
Most of these targets are located in Southeast Asia, in countries such as Malaysia, Indonesia, China, and India, where the most recent attack took place.
Hotpatching operations need administrator-level permissions
Microsoft says that the group is still active and that there's still a way for companies to avoid infection. The company's security experts explain that hotpatching operations need to run from under an admin user, which means Platinum threat actors first have to infect each target.
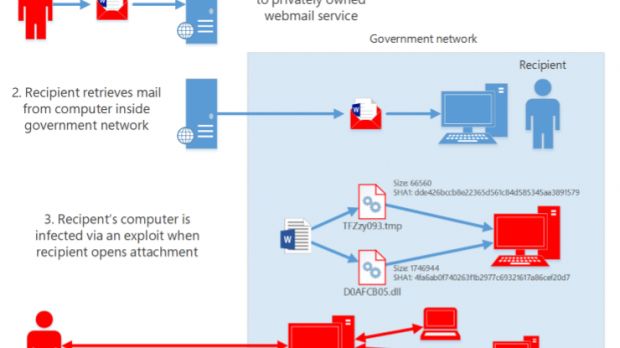
In its report, Microsoft adds that the group has been doing this by sending spear-phishing emails that come with boobytrapped Office documents.
These documents, when opened, employ well-known vulnerabilities or never-before-seen zero-day exploits to infect computers with malware that gains admin privileges and later runs a malicious hotpatching operation.
"The monetary investment required to collect and deploy zero-day exploits at this level is considerable," Microsoft notes in its report, hinting at the fact that the group might be sponsored by a large criminal organization or a state actor.
Hotpatching, as a technique in general, is not exclusive to Windows machines. Crooks used hotpatching tools this past autumn and winter to push malicious updates to iOS apps, bypassing Apple's App Store review process.
 14 DAY TRIAL //
14 DAY TRIAL //