Microsoft rolled out the first Windows XP update after three years in an attempt to protect customers from getting infected with WannaCry, and now the company says governments should treat vulnerabilities in a different way because civilians are the very first ones affected every time such an accident happens.
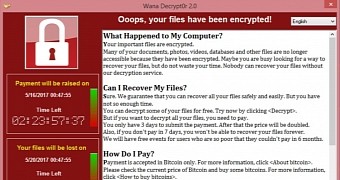
Thousands of computers across the world were infected since Friday with a new ransomware called WannaCry which locks down PCs and asks for a $300 ransom to restore access to files. The infection is based on a vulnerability that was stolen from the NSA earlier this year and which was published online by hacking group Shadow Brokers.
The affected organizations include state departments in several large countries, as well as health institutions like the British NHS. Microsoft said on Friday that systems running fully up-to-date versions of supported Windows were protected, and decided to also release an update for computers with older Windows versions, like XP and Server 2003, to block the ransomware.
In a statement today, Brad Smith, President and Chief Legal Officer at Microsoft, confirms that the exploit was patched on March 14 for Windows users, confirming that attacks are based on the NSA vulnerability that got leaked accidentally.
Update, update, update
Smith emphasizes that it’s critical for customers worldwide to update their systems to remain protected, explaining that while some organizations need time for testing, Microsoft is also spending more time to certify updates before shipping them.
“As cybercriminals become more sophisticated, there is simply no way for customers to protect themselves against threats unless they update their systems. Otherwise they’re literally fighting the problems of the present with tools from the past,” Smith explained.
Eventually, Smith also calls for governments to treat these issues seriously, pointing out that agencies should no longer create a “stockpile of vulnerabilities,” but instead report them to the vendor.
“This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage,” he said.
One possible solution to prevent these cases in the future is to adopt the Digital Geneva Convention that would make it a requirement for governments to report vulnerabilities to vendors, “rather than stockpile, sell, or exploit them.”
 14 DAY TRIAL //
14 DAY TRIAL //