Crooks are targeting government and educational institutions with a new ransomware family named MarsJoke (or JokeFromMars), discovered in late August, but which came to life this week through a massive email spam wave.
The group behind this ransomware is using emails disguised as air travel confirmation notifications, which also contain a link to a downloadable EXE file.
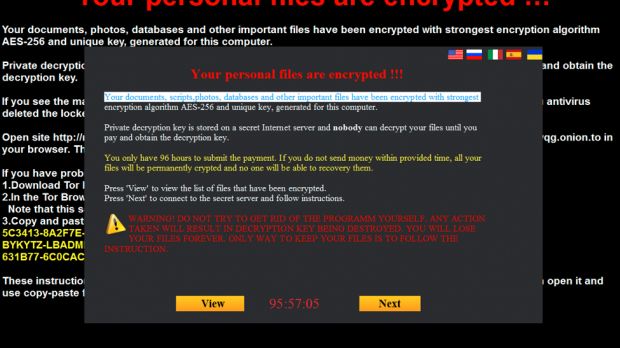
Running this file installs the MarsJoke ransomware, which locks the user's data with the AES-256 encryption algorithm. Once the ransomware locks the files, it asks the user to pay 0.7 Bitcoin, which is around $320 at the time of writing.
MarsJoke copies the CTB-Locker visual style
The ransomware, discovered by Proofpoint researcher Darien Huss, replaces the user's desktop wallpaper and leaves ransom notes in HTML and TXT format in every folder it locks files, in order to get the user's attention.
The visual style is copied from the more successful CTB-Locker ransomware, but MarsJoke does not claim to be CTB-Locker, unlike other ransomware variants that try to pass as something more dangerous and hard to decrypt.
At the time of writing, there is no decrypter available for MarsJoke that allows victims to recover locked files.
MarsJoke distributed via the Kelihos botnet
To decrypt their files, victims have to install the TOR Browser and access a website hosted on the Tor network.
The ransomware's name comes from a string found in its source code that reads "HelloWorldItsJokeFromMars."
Independent security researcher Gary Warners has also written about the MarsJoke ransomware, discovering that the spam emails came from machines part of the Kelihos botnet, a network of infected computers used to send spam or relay malicious proxy traffic.
At the time MarsJoke was first deployed in small tests in late August, the Kelihos botnet also tripled in size in just 24 hours, a clear sign that crooks were readying for massive operations.
A focus on government institutions
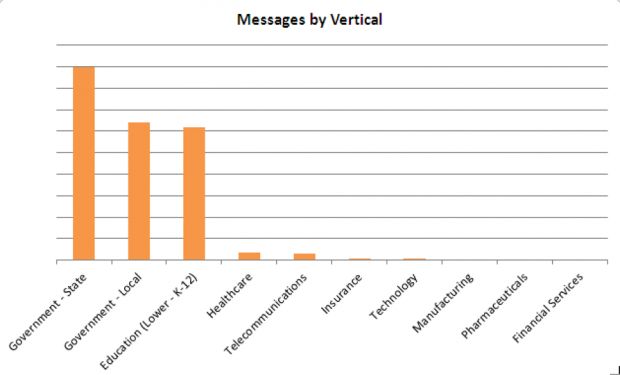
Based on the email addresses targeted via this recent spam campaign started on September 22, three verticals have faced the brunt of the attack: state government, local government, and K-12 educational institutions.
The same verticals have been targeted via a similar massive spam campaign just days before researchers discovered MarsJoke. In that spam flood, also discovered by Proofpoint, crooks deployed the CryptFile2 (or CryptMix) ransomware.
For what it's worth, this gang of criminals seems to be smarter than most of their counterparts that deploy ransomware in a shotgun approach, trying to infect whoever they can.
By going after government institutions, they might get lucky and infect a target that has failed to implement a proper backup procedure, effectively shutting down its system until a ransom has been paid. The chances of squeezing a ransom payment out of these targets are higher than with regular home users.
 14 DAY TRIAL //
14 DAY TRIAL //