A little bit late with its year-in-review report is Dell, who has just recently released the Dell Security Annual Threat Report that summarizes all the major threats the company saw and dealt with during the past year.
Dell's experts are saying that, in 2015, their security products logged more than 64 million unique malware samples, which represented a 73% rise from 2014 (37 million) and a tripling of 2013's numbers.
Additionally, the company also blocked 2.17 trillion IPS (Intrusion Prevention System) attacks and 8.19 billion malware attacks, the last figure representing twice the numbers recorded in 2014 (4,2 billion).
Dell isn't exaggerating in its assessments. Similar numbers were also reported by Panda Security a month ago, when the company announced it detected 84 million new malware families and 304 million total malware samples in 2015, which represented 27.63% of the total number of malware families ever discovered.
So there's a noticeable surge in malware numbers, which many security providers are also noticing, not just Dell. The company also saw a few clear trends during the past year, some of which were apparent to anyone reading our news section as well.
2015: Android malware and exploit kits
First of all, Android malware continued to grow in numbers during 2015, something that experts also expect to happen in 2016 as well. Dell saw an increase in ransomware infections, but also a growth of banking trojans targeting the Android OS.
Furthermore, exploit kit (EK) usage exploded during the past year, and kits like Angler, Nuclear, Magnitude and Rig were the tools that dominated the EK landscape.
In 2015, most exploit kits added upgrades to their code, such as the usage of a more complex anti-forensic mechanism to evade security software, frequent URL pattern changes to evade easy detection, and new URL redirection techniques to direct users towards the kit's landing page, where the user infection would occur.
As for new trends for malware construction, the usage of SSL/TLS encryption for C&C communications continued to rise, making the life of security researchers even harder than before.
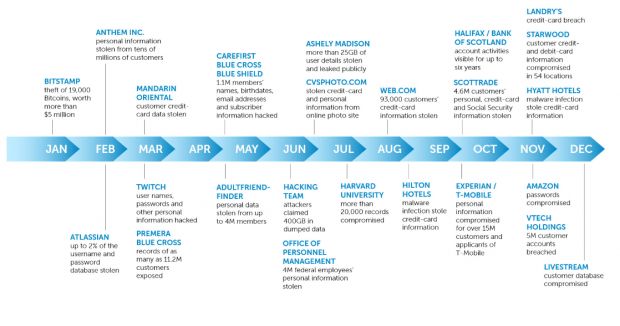
Below is a timeline of the most infamous cyber-attacks and data breaches from the past year.

 14 DAY TRIAL //
14 DAY TRIAL //