A week after it revealed how Android malware uses the "target_sdk" attribute to bypass security features on Android Marshmallow (6.0), Symantec is now presenting technical details about two other methods used by crooks to skirt Android's defensive features once again.
As before, the culprits are the Android.Bankosy banking trojan and the Android.Cepsohord click-fraud bot, whose authors are apparently scouring GitHub projects for tricks on how to get a list of active processes (running tasks).
Discovering the list of active tasks is critical to malware creators since it allows them to sniff out the user's current applications and show a malicious phishing overlay on top to collect login credentials.
Previously, in Android versions before Lollipop (5.0), crooks performed this action with the getRunningTasks() API call, which was removed in Lollipop and subsequent versions.
Method 1: Reading the "/proc/" system file
The first technique discovered by Symantec was taken from the AndroidProcesses GitHub project by Jared Rummler. His app is not malicious in any way, but the crooks have stolen some of its code and are using it to get a list of current apps.
Rummler's method relies on reading the "/proc/" file to list all currently running processes. Malware coders read the output of this file to find the current app running in the phone's foreground.
Symantec says this technique works on Android Lollipop and Marshmallow, but not the recent N snapshot.
Method 2: Using the UsageStatsManager API
The second trick borrows from the same project, but also from a project by GeeksOnSecurity, called Android Malware Example, which is, you guessed it, proof-of-concept Android malware.
The method uses the UsageStatsManager API to get a list of running processes. This API provides historical data detailing the device's usage history, including past used apps.
Symantec says that Android.Bankosy and Android.Cepsohord employ this API to query for apps used in the last two seconds and based on which they determine the currently running app.
Luckily for users, UsageStatsManager API requires users to give the malware special privileges to access its output.
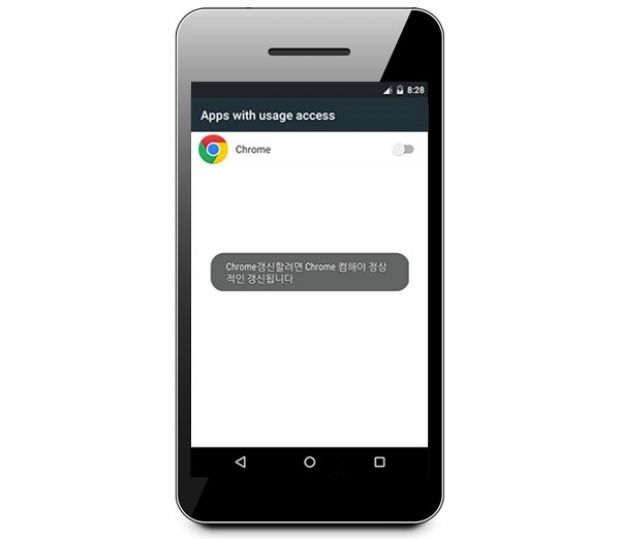
To go around this limitation, the crooks use a fake overlay to ask for the permission, disguising their app's name and icon as Chrome's, as in the image below. Symantec says that this overlay is created using the code found in GeeksOnSecurity's proof-of-concept malware. Symantec says this technique doesn't work on certain Android OEMs, like Samsung.

 14 DAY TRIAL //
14 DAY TRIAL //