The Media Trust, an online security vendor, has detected a malvertising campaign that specifically targeted ads presented with online video as a channel of distribution.
While malvertising campaigns using video ads had surfaced in the past, the recent attack detected by The Media Trust affected over 3,000 websites, many of which were part of Alexa's Top 100. Fortunately, the campaign only lasted for 12 hours, late on Thursday, October 29, and was thwarted by the company's quick response.
The attack followed the regular infection pattern used by normal malvertising techniques, but with a few modifications to work with video delivery platforms.
According to The Trust Media team, a malicious SWF file was downloaded on the victim's computers when accessing a video page. The malicious file was hosted on the brtmedia.net domain and was imitating a video player.
This SWF file executes its malicious load only on less-known sites, avoiding large video platforms, where security teams continually search their sites looking for problematic ads.
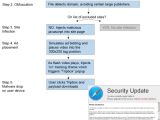
The actual attack happens when the SWF file injects JavaScript code in the page where the video ad is supposed to be displayed, simulating a winning ad bid, but actually loading a 1px by 1px hidden iframe.
This iframe loads a popup window that scans the user's computer settings and prompts them with a message to update some of their local software.
If the user is careless to click on the popup, they will download malicious software packed with PUPs and other malware.

 14 DAY TRIAL //
14 DAY TRIAL //