A recent malvertising campaign has been seen on six of Spain's biggest torrent sites, exposing around 84.2 million users to the CryptoWall ransomware.
The campaign was possible and was more efficient than similar ones because the attackers managed to install a backdoor in Publited's servers, the ad network that delivered the advertisements on those sites.
A rare occurrence of a compromised ad network
An ad network having their servers hacked is a rare occurrence, but this resulted in a much more dangerous situations for users, allowing the attackers to better control the way the malicious ads are displayed to users.
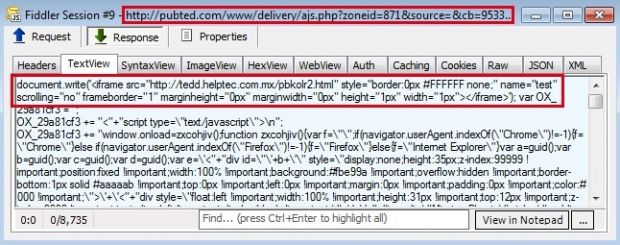
While in most cases malvertisers can only show ads by bidding and winning ad spots, and then corrupting its delivery method via malicious JavaScript files and countless redirects, by controlling the ad platform, attackers were able to inject malicious iframes along with legitimate ads, and make them look like they would be coming from the ad server itself.
Furthermore, attackers were also able to set complicated traffic filters in place, and control to whom, where, and when the malicious ads were being shown to.
Attackers had complete control over the flow of malicious ads
So if malvertisers would have liked to show malicious ads on pages where users downloaded the latest Hollywood movie releases, between 7 PM and 11 PM, and only to users from southern Spain, they would have been able to do this with no difficulty at all.
The malicious iframes inserted into legitimate ads led users to pages where the Neutrino exploit kit was served, which then infected users with the CryptoWall ransomware.
This went on for most of the campaign, but as Malwarebytes reports, the Angler exploit kit was also used in the later stages.
Malwarebytes informed Publited of the campaign, and worked with the ad network to remove the attackers' backdoors from their infrastructure.
We have contacted Publited for comment.
UPDATE: After we received an answer from Publited, we amended our article where we said that they're server was compromised. According to a Publited spoksesperson, "The servers never were compromised, the hacker only can inject some code in the php files. The bug was solved and we improved and increased the security of the servers to avoid this kind of situation."
 14 DAY TRIAL //
14 DAY TRIAL //