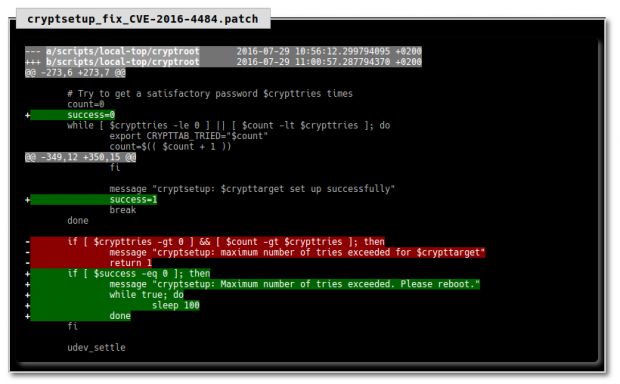
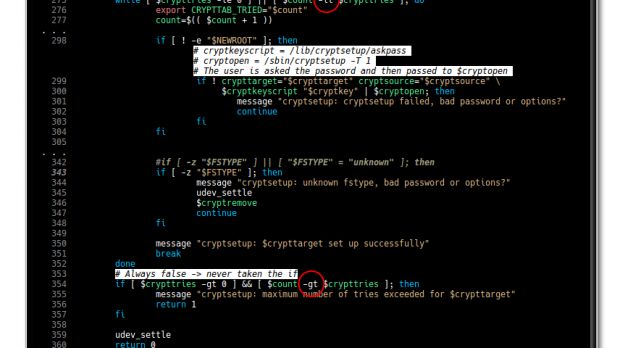
According to a recent security advisory published by Hector Marco and Ismael Ripoll as CVE-2016-4484 and entitled "Cryptsetup Initrd root Shell," it would appear that there's a major vulnerability in Cryptsetup affecting many GNU/Linux systems.
Cryptsetup is a command-line utility designed for setting up a new dm-crypt device in LUKS (Linux Unified Key Setup) encryption mode, a.k.a. disk encryption, on a Linux-based operating system. The recently discovered vulnerability appears to exist in the scripts that are used by the Cryptsetup utility to unlock the LUKS-encrypted system partition.
As the vulnerability does not appear to depend on a certain configuration or system, it affects numerous GNU/Linux distributions based on Debian or Red Hat Enterprise Linux (RHEL), including the popular Ubuntu and Fedora, allowing an attacker to access the root initramfs shell on the affected system, or remotely exploit cloud environments.
"Attackers can copy, modify or destroy the hard disc as well as set up the network to exfiltrate data. This vulnerability is specially serious in environments like libraries, ATMs, airport machines, labs, etc, where the whole boot process is protect (password in BIOS and GRUB) and we only have a keyboard or/and a mouse," reads the security advisory, which was presented at the DeepSec 2016 conference in Vienna, Austria.
A patch is now available for affected distributions
If you're wondering right now if your GNU/Linux distribution is affected by said vulnerability, you should know that if you're running Ubuntu or Debian and you have an encrypted LUKS partition, the OS is most certainly vulnerable. The security advisory also informs users of the Fedora 24 Linux operating system that their distributions using Dracut instead of initramfs are affected as well.
But don't despair, because a patch is already available and it should soon land in the software repositories of your favorite GNU/Linux distro, so make sure that you are always using the most recent package versions and your OS is up to date. To see if your system is vulnerable, press the Enter key for about 70 seconds at the LUKS password prompt until a shell appears. Arch Linux users are not affected by this issue, nor are Solus users.
 14 DAY TRIAL //
14 DAY TRIAL //