The patch that Apple applied to Mac OS X to fix the GateKeeper vulnerability discovered last September was insufficient to protect users, as Patrick Wardle, the researcher that first discovered it, said in a blog post on his company's blog.
Back in September, Mr. Wardle was warning users that GateKepper, one of Apple's security watchdogs, was slacking at his job.
Apple introduced GateKeeper as a real-time scanning system to prevent the installation of malicious applications, either from disk, or from online sources. For an app to install, it would have to present a trusted certificate to GateKeeper.
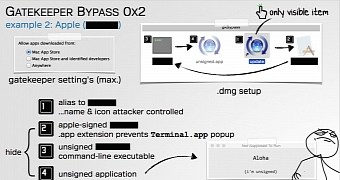
Mr. Wardle found out that this was only a one-time static check, when the app was installed. If an application could load binaries and then execute those apps, GateKeeper would not check these dynamically loaded files.
Attackers could craft malicious applications and then place them in a dedicated folder inside an app's directory, tricking the app into loading malicious code without GateKeeper ever raising an eyebrow.
Apple did a poor job at fixing the GateKeeper flaw
Apple said it fixed this issue with the release of Mac OS X El Capitan 10.11.1. Mr. Wardle discovered that this was not a patch, as Apple said, but only a simple blacklist.
He said that Apple didn't bother fixing the cause of the issue, and only made XProtect, another Mac security tool, blacklist the binaries that could be abused in this manner, and trick other apps into installing malware.
Basically, Apple blacklisted a small list of files that Mr. Wardle included in his examples, instead of creating a system that could detect when trusted apps were being abused in this manner.
The way in which Apple decided to fix this serious security hole leaves many security experts scratching their heads and asking themselves "what was Apple thinking?"
Below is a proof-of-concept video provided by Patrick Wardle. Mr. Wardle will be presenting more details about GateKeeper at the ShmooCon security conference on January 17.
 14 DAY TRIAL //
14 DAY TRIAL //