Mustafa Al-Bassam, aka tFlow, co-founder of the LulzSec hacking crew, has published today more details about how the GCHQ used the covert Joint Threat Research Intelligence Group (JTRIG) to attack hacktivism crews. Besides, it seems that they also tried to influence elections in Iran and boost and help the Arab Spring uprising in Syria.
His report is based on a first-hand experience, as part of the LulzSec crew attacked by JTRIG, on documents leaked by Edward Snowden in 2014, and on his own research on the subject, with Al-Bassam having made the jump from hacker to security consultant this past March.
JTRIG did more than just attack hacktivism groups
JTRIG's operations came to light in 2014, when The Intercept published a set of documents from the massive Edward Snowden leak.
These documents revealed the existence of JTRIG as a special unit inside GCHQ, tasked with carrying out social engineering attacks meant to infiltrate and gather intelligence on online hacktivism crews.
These documents showed that JTRIG and the GCHQ launched DDoS attacks on various IRC servers that groups like LulzSec and Anonymous used to plan operations.
JTRIG was behind Lurl.me
Today, Al-Bassam has revealed that JTRIG used a URL shortener for many different operations, including one to compromise a fellow hacker named P0ke.
He says the agency set up the Lurl.me URL shortening service and used it to mask links to various sites. They used Lurl.me to hide malicious sites that delivered code meant to help the GCHQ deanonymize P0ke's location and identity.
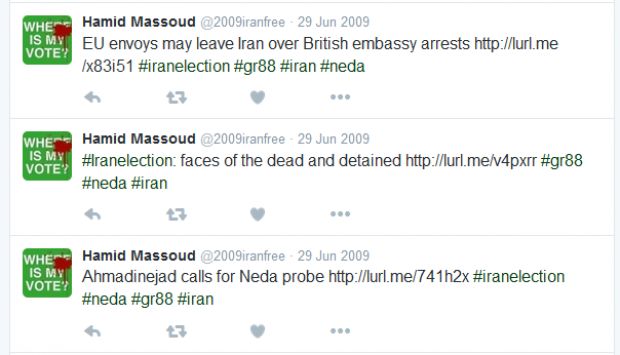
Al-Bassam says this happened in 2010. Based on his research, the Lurl.me service existed online between 2009 and 2013.
His research uncovered a plethora of tweets containing Lurl.me links. There were two main sets of Twitter campaigns that involved this URL shortening service. The first took place in 2009, during the Iran elections, something confirmed by the leaked Snowden documents, which read:
“ [T]he Iran team currently aims to achieve counter-proliferation by: (1) discrediting the Iranian leadership and its nuclear programme; (2) delaying and disrupting access to materials used in the nuclear programme; (3) conducting online HUMINT; and (4) counter-censorship. ”
Al-Bassam says that JTRIG employees managed several social media accounts that were tweeting out dissident material to discredit Iran's leadership, all using the Lurl.me service.The @2009iranfree account was the most active. The account still exists today but has ceased any activity in 2009, with Lurl.me links still visible on its timeline at the time of writing.
After trying to influence public opinion in Iran using Twitter, JTRIG seems to have stopped using lurl.me for an entire year, with no lurl.me links being spotted in 2010 at all.
JTRIG used Lurl.me for influencing politics in the Middle East
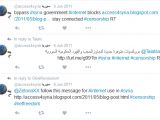
Al-Bassam explains that new links popped up all of a sudden in 2011, just in time for the Arab Spring demonstrations in Syria. In this case, most of the tweets came from @access4syria, a very active account.
"The account was only active between May and June 2011, and only tweeted between 9 AM and 5 PM UK time on Monday to Friday," Al-Bassam notices. This time around, agents also used Blogspot to run as well, with JTRIG taking a position against the Assad regime.
In both campaigns, the tweets containing Lurl.me links were advertised as a way to read materials blocked by the regime. In both campaigns, users engaged with the accounts, and many quoted or retweeted the links.
JTRIG was luring Syrians to use a boobytrapped proxy
The tweets on this account kept promoting a Blogspot article that advertised two proxies for Syrians to use and access the Internet in case it was blocked.
Al-Bassam makes the connection between these proxies and the GCHQ MOLTEN-MAGMA hacking tool, a CGI HTTP Proxy with the ability to log all traffic and perform HTTPS MitM attacks, snooping on encrypted traffic.
Curiously, the Lurl.me URL shortener shut down in 2013, after Snowden started leaking all sorts of NSA and GCHQ documents.

 14 DAY TRIAL //
14 DAY TRIAL //