A trojan coded in Lua is targeting Linux platforms with the goal of adding them to a global botnet with the purpose of carrying out DDoS attacks, security researcher MalwareMustDie! has reported today.
For an operating system with a minuscule 2.11 percent market share, this is our third story on Linux malware in the past 24 hours, after previously reporting on the Mirai DDoS trojan and the Umbreon rootkit.
LuaBot falls into the same category as Mirai because its primary purpose is to compromise Linux systems, IoT devices or web servers, and add them as bots inside a bigger botnet controlled by the attacker.
LuaBot most likely used for DDoS attacks
At the moment, the LuaBot trojan is packed as an ELF binary that targets ARM platforms, usually found in embedded (IoT) devices. Based on MalwareMustDie's experience, this seems to be the first Lua-based malware family packed as an ELF binary spreading to Linux platforms.
An initial analysis by MalwareMustDie didn't uncover any malicious functionality outside the capabilities of adding devices to a centrally controlled botnet. One day after publishing his research on LuaBot, MalwareMustDie received an extra sample, a LuaBot module, which when installed, granted LauBot the ability to carry out Layer 7 DDoS attacks.
Unlike Mirai, which is the fruit of a two-year-long coding frenzy, LuaBot is in its early stages of development, with the first detection being reported only a week ago and a zero detection rate on VirusTotal for current samples.
Since it's only a one-week-old malware strain, details are scarce about its distribution and infection mechanism.
LuaBot author challenges security researchers
MalwareMustDie has managed to reverse-engineer some of the trojan's code and discovered that the bot communicates with a C&C server hosted in the Netherlands on the infrastructure of dedicated server hosting service WorldStream.NL.
The researcher also found that LuaBot's brazen developer left a message behind for all the infosec professionals trying to deconstruct his code. The message reads, "Hi. Happy reversing, you can mail me: [REDACTED .ru email address]."
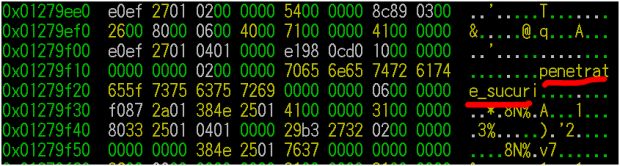
Additionally, MalwareMustDie also discovered code labeled as "penetrate_sucuri," alluding to features capable of skirting Sucuri's infamous Web Application Firewall, a cyber-security product that has stopped many web threats in the past.
MalwareMustDie told Softpedia that "it seems the function is there [...] coded with that purpose," but the researcher later admitted that "I don't know the Sucuri WAF much, so I can not test it." Softpedia has reached out to Sucuri, and we'll update the article if this function proves to be a successful firewall bypass or just a piece of unfinished code.
UPDATE [September 6, 2016]: Article was updated to include later analysis of the LuaBot DDoS module.
UPDATE [September 19, 2016]: More analysis from MalwareMustDie revealed the true purpose of this malware. "Exploitation of vulnerable routers for botnet for selling socks to cyber crime," MalwareMustDie told Softpedia. "Using DDoS, not main function, mostly for personal use." So basically, the malware coder is using your routers as proxies to relay malicious traffic, whatever that may be.

 14 DAY TRIAL //
14 DAY TRIAL //